Get complete RPSC Vice Principal ITI Computer Science Engineering (CSE) solved questions with detailed explanations. Practice previous year papers, boost your subject knowledge, and prepare effectively for the RPSC ITI Vice Principal exam with authentic and accurate solutions.
In addition, this solution guide is not just about answers, it is designed as a learning companion. By studying these explanations, students can strengthen their problem-solving skills and approach future exams with greater clarity and confidence.
| Unit | Unit Name | Description |
|---|---|---|
| Unit 1 | Digital Logic Circuits and Components | Digital Computers, Logic Gates, Boolean Algebra, Map Simplifications, Combinational Circuits, Flip-Flops, Sequential Circuits, Integrated Circuits, Decoders, Multiplexers, Registers and Counters, Memory Unit. Data Representation: Data Types, Number Systems and Conversion, Complements, Fixed Point Representation, Floating Point Representation, Error Detection Codes, Computer Arithmetic - Addition, Subtraction, Multiplication and Division Algorithms. Central Processing Unit: General Register Organization, Stack Organization, Instruction Formats, Addressing Modes, RISC Computer, CISC Computer. |
| Unit 2 | Discrete Mathematics | Propositional and Predicate Logic, Propositional Equivalences, Normal Forms, Predicates and Quantifiers, Nested Quantifiers, Rules of Inference. Sets and Relations: Set Operations, Representation and Properties of Relations, Equivalence Relations, Partially Ordering. Counting, Mathematical Induction and Discrete Probability: Basics of Counting, Pigeonhole Principle, Permutations and Combinations, Inclusion- Exclusion Principle, Mathematical Induction, Probability, Bayes’ Theorem. Graph Theory: Simple Graph, Multigraph, Weighted Graph, Paths and Circuits, Shortest Paths in Weighted Graphs. |
| Unit 3 | Computer Organization and Architecture | RAM and ROM, Machine instructions, Addressing modes, Memory interface, I/O interface (Interrupt and DMA mode), Microcontrollers, Interfacing, Instruction pipelining, Cache and main memory, Secondary storage. |
| Unit 4 | Programming | Programming in C++: Tokens, Identifiers, Variables and Constants, Data types, Operators, Control statements, Functions Parameter Passing, Virtual Functions, Class and Objects, Constructors and Destructors, Overloading, Inheritance, Templates, Exception and Event Handling, Streams and Files, Multifile Programs, Object, Class, Inheritance, Polymorphism, Dynamic binding, access modifier. |
| Unit 5 | Data Structures and Algorithms | Asymptotic notation, Notions of space and time complexity, Worst and average case analysis. Arrays and their Applications. Sparse Matrix, Stacks, Queues, Priority Queues, Linked Lists, Trees, Forest, Binary Tree, Threaded Binary Tree, Binary Search Tree, AVL Tree, B Tree, B+ Tree, B* Tree, Graphs, Sorting (Bubble, Heapsort, insertion, Selection, Quicksort) and Searching Algorithms. Hashing. Divide and Conquer, Dynamic Programming, Greedy Algorithms, Backtracking, Branch and Bound, Graph Algorithms: Breadth-First Search, Depth-First Search, Shortest Paths, Maximum Flow, Minimum Spanning Trees. |
| Unit 6 | Operating System | Operating System Structure, Operations and Services; System Calls, Operating-System Design and Implementation; System Boot. Process Management: Process Scheduling and Operations; Inter-process Communication, Communication in Client–Server Systems, Process Synchronization, Critical-Section Problem, Semaphores, Synchronization. Threads: Multicore Programming, Multithreading Models, Threading Issues. CPU Scheduling: Scheduling Criteria and Algorithms; Thread Scheduling. Deadlocks: Deadlock Characterization, Methods for Handling Deadlocks, Deadlock Prevention, Avoidance and Detection; Recovery from Deadlock. Memory Management: Contiguous Memory Allocation, Swapping, Paging, Segmentation, Demand Paging, Page Replacement, Allocation of Frames, Thrashing, Memory-Mapped Files. Storage Management: MassStorage Structure, Disk Structure, Scheduling and Management, RAID Structure. |
| Unit 7 | Database System Concepts and Architecture | Data Models, Schemas, and Instances. Three-Schema Architecture and Data Independence. Database Languages and Interfaces. Data Modeling: Entity-Relationship Diagram, Relational Model - Constraints, Languages, Design, and Programming, Relational Database Schemas, Update Operations and Dealing with Constraint Violations. SQL: Data Definition and Data Types, Constraints, Queries, Insert, Delete, and Update Statements. Views, Stored Procedures and Functions. Database Triggers, SQL Injection. Normalization for Relational Databases: Functional Dependencies and Normalization. Algorithms for Query Processing and Optimization. Transaction Processing, Concurrency Control Techniques, Database Recovery Techniques, Object and Object-Relational Databases. Database Security and Authorization. |
| Unit 8 | Software Engineering | Process and Life cycle Models, information gathering, requirement and feasibility analysis, data flow diagrams, UML, process specifications, input/output design, planning and managing the project, design, coding, testing, implementation, maintenance, Introduction to Agile technology. |
| Unit 9 | Data Communication | Components of a Data Communication System, Simplex, Half Duplex and Duplex Modes of Communication. Analog and Digital Signals. Noiseless and Noisy Channels. Bandwidth, Throughput and Latency. Digital and Analog Transmission. Data Encoding and Modulation Techniques. Broadband and Baseband Transmission. Multiplexing, Transmission Media, Transmission Errors, Error Handling Mechanisms. Computer Networks: Network Topologies, Local Area Networks, Metropolitan Area Networks, Wide Area Network, Wireless Networks, Internet. Network Models: Layered Architecture, OSI Reference Model and its Protocols, TCP/IP Protocol Suite, Physical, Logical, Port and Specific Addresses, Switching Techniques. Functions of OSI and TCP/IP Layers: Framing, Error Detection and Correction, Flow and Error Control; Sliding Window Protocol, HDLC, Multiple Access – CSMA/CD, CSMA/CA, Reservation, Polling, Token Passing, FDMA, CDMA, TDMA, Network Devices, Backbone Networks, Virtual LANs. IPv4 Structure and Address Space, Classful and Classless Addressing. Datagram, Fragmentation and Checksum. IPv6 Packet Format, Mapping Logical to Physical Address (ARP). |
| Unit 10 | Current Technologies | Network Security- Malwares, Cryptography and Steganography. Secret-Key Algorithms, Public-Key Algorithms, Digital Signature, Virtual Private Networks, Firewalls. Mobile Technology: GSM and CDMA, Services and Architecture of GSM and Mobile Computing. Middleware and Gateway for Mobile Computing; Mobile IP and Mobile Communication Protocol. Cloud Computing and IoT: SaaS, PaaS, IaaS, Public and Private Cloud; Virtualization, Virtual Server, Cloud Storage, Database Storage, Resource Management, Service Level Agreement, Basics of IoT. Introduction to AI, Knowledge representation, Fuzzy Logic, Natural Language Processing. |
| Exam Name | RPSC Vice Principal (Superintendent) ITI Exam CSE (Computer Science Engineering) Paper : 2024 | |
|---|---|---|
| Exam Date | 30th July 2025 | |
| S.N. | Name of Subjects | No. of Questions Asked |
| 01. | Programming Languages (C++) | 15 |
| 02. | Data Structure and Algorithms (DSA) | 15 |
| 03. | Discrete Mathematics (DM) and Statistics | 16 |
| 04. | Computer Organization and Architecture (COA) | 10 |
| 05. | Operating System (OS) | 20 |
| 06. | Digital Electronics and Circuits (DEC) | 10 |
| 07. | Database Management System (DBMS) & Structured Query Language (SQL) | 20 |
| 08. | Software Engineering & SAD | 10 |
| 09. | Computer Networks (CN) / Data Communication | 20 |
| 10. | Networks Security and Cryptography / Current Technologies | 14 |
Q: A sender wants to compute the checksum for the ASCII text "RPSC". Which of the following is the correct 16-bit checksum (in hexadecimal) for the string "RPSC"? Given that each character's ASCII hexadecimal equivalent ('R' → 0x52, 'P' → 0x50, 'S' → 0x53, 'C' → 0x43).
5A6C
5B6D
A593
6A5C
[ Option A ]
A Checksum is a simple method used in data communication to detect errors in transmitted messages. The basic idea is to sum the numerical values of all data units using one’s complement arithmetic (end-around carry) , and then taking the one’s complement of the final sum.
End-around carry means add MSB carry-out back into LSB for one’s-complement addition.
Q: How many times the following C program prints “Hello”?
main()
{
fork();
fork();
printf(“Hello”);
}
Twice
Four Times
Six Times
Only Once
[ Option B ]
The fork() System Call
The fork() system call in C is used to create a new process by duplicating the existing one.
After a fork() call, there are two processes running the same code, the parent process and the child process. Each process continues execution from the point where the fork() was called. So, if you call fork() multiple times, the number of processes increases exponentially.
There is no loop, and each fork() doubles the number of processes. Hence, total “Hello” prints = 2number of forks
Finally, 22 = 4.
Q: In GSM Architecture, which of the following stores the local copy of the data from the HLR?
MSC
VLR
AUC
Mobile Station
[ Option B ]
In GSM architecture, the Home Location Register (HLR) is a central database that stores permanent subscriber information, such as the subscriber’s profile, services, and current location. When a subscriber roams into a new area, the Visitor Location Register (VLR) temporarily stores a local copy of the subscriber’s data from the HLR.
Q: A technique called __________ can be used by malicious hackers to steal data or damage the database.
SQL injection
SQL assertion
SQL trigger
SQL procedure
[ Option A ]
SQL Injection is a malicious technique in which attackers provide crafted input to SQL queries, tricking the database into executing unintended commands. This can lead to unauthorized data access, modification, or deletion. It is a major security concern for databases connected to web applications.
Q: Three vertices of a regular hexagon are chosen. A triangle is formed with these three chosen vertices. The probability, that this triangle is equilateral, is
1/2
1/5
1/10
1/6
[ Option C ]
To find the probability that a triangle formed by choosing three vertices of a regular hexagon is equilateral, we proceed step by step.
Step 1: Total number of triangles
A hexagon has 6 vertices. The number of ways to choose any 3 vertices to form a triangle is calculated using combinations:
C(6,3) = 20
So, there are 20 possible triangles in total.
Step 2: Favorable outcomes (Equilateral Triangles)
In a regular hexagon, an equilateral triangle can be formed by choosing every second vertex. Label the vertices as 1, 2, 3, 4, 5, 6 clockwise. The equilateral triangles possible are:
Triangle (1, 3, 5)
Triangle (2, 4, 6)
Thus, there are 2 favorable triangles.
Step 3: Probability
The probability is given by:
P = Favorable outcomes / Total outcomes = 2 / 20 = 1/10
Q: In a paging system with a Translation Lookaside Buffer (TLB), the TLB has a hit ratio of 80%. It takes 20 nanoseconds to search the TLB and 100 nanoseconds to access main memory. What is the effective memory access time?
120 nanoseconds
140 nanoseconds
160 nanoseconds
180 nanoseconds
[ Option B ]
Q: Which of the following is not range of frequency band operate in Industrial Scientific and Medical (ISM)?
902 – 928 MHz
2.4 – 4.835 GHz
5.725 – 5.850 GHz
1.5 – 1.6 GHz
[ Option D ]
Industrial, Scientific, and Medical (ISM) bands are portions of the radio spectrum reserved internationally for non-commercial purposes like industrial heating, medical equipment, and scientific experimentation. Over time, they have also been widely used for unlicensed wireless communication, such as Wi-Fi and Bluetooth.
Q: Which of the following are respectively correlated with reliability, performance, and supportability in context of FURPS developed by Hewlett-Packard, the target software design quality attributes namely functionality, usability, reliability, performance, and supportability?
Consistency, Response time, Efficiency
Mean-time-to-failure, Throughput, Maintainability
Compatibility, Accuracy of Results, Fast recovery from failure
Fast recovery from failure, Consistency, Security
[ Option B ]
The FURPS (Functionality, Usability, Reliability, Performance, Supportability) Model, developed by Hewlett-Packard (HP), is a well-known framework used to classify software quality attributes.
| ATTRIBUTE | MEANING |
|---|---|
| Functionality | Accuracy, correctness, and suitability of the software to perform its intended functions. |
| Usability | Ease of use, learnability, and user-friendliness of the system. |
| Reliability | Mean-Time-To-Failure (MTTF), how long the software runs without failure. A higher MTTF means the system runs longer without failure. |
| Performance | Throughput, Response Time, how efficiently the system performs, including speed and capacity. Throughput measures how many operations or transactions the system can process in a given time. |
| Supportability | Maintainability, ease of making changes, fixing bugs, and updating the system. Maintainability reflects how easily the system can be modified or corrected. |
Q: What is the full form of SDRAM?
Synchronous Dynamic Random Access Memory
Synchronous Data Random Access Memory
Synchronous Dynamic Random Access Message
Synchronous Data Random Access Message
[ Option A ]
The full form of SDRAM is Synchronous Dynamic Random Access Memory. SDRAM is a type of dynamic RAM that is synchronized with the system clock, meaning it waits for the clock signal to perform read or write operations. This synchronization improves speed and efficiency compared to conventional DRAM.
Additionally, SDRAM can pipeline commands, allowing multiple instructions to be processed simultaneously.
Q: The logical output of EX-NOR gate is:
(A'.B + A. B')
(A.B + (A.B)')
(A'.B' + A.B')
(A.B + A'.B')
[ Option D ]
The EX-NOR (Exclusive-NOR) gate is the complement of the EX-OR (Exclusive-OR) gate. While an EX-OR gate gives output 1 when the inputs are different, the EX-NOR gate gives output 1 when the inputs are the same that means, both inputs are 0 or both are 1.
| Input A | Input B | Output (A ⊙ B) |
|---|---|---|
| 0 | 0 | 1 |
| 0 | 1 | 0 |
| 1 | 0 | 0 |
| 1 | 1 | 1 |
The Boolean expression for an EX-NOR gate is:
Y=A⊙B = (A⊕B)’ = A.B+A’B’
Q: An attempt to divide by zero results in which type of interrupt?
External Interrupt
Internal Interrupt
Software Interrupt
Power failure Interrupt
[ Option B ]
An Interrupt is a signal that temporarily halts the CPU’s current execution to handle an event. Interrupts are classified into internal and external types:
A divide-by-zero operation is an error generated by the CPU itself, so it is an internal interrupt.
| TYPE OF INTERRUPT | DESCRIPTION | EXAMPLES |
|---|---|---|
| Internal Interrupt | Generated by the CPU due to an error or specific condition during execution. | Divide by zero, invalid opcode, overflow. |
| External Interrupt | Generated by external devices or events outside the CPU. | Keyboard input, mouse click, timer, power failure. |
| Software Interrupt | Initiated by a program instruction to request a service from the operating system. | System calls, INT instruction in assembly. |
| Power Failure Interrupt | Triggered when there is a sudden loss or fluctuation of power. | UPS signals, sudden shutdown detection. |
| Hardware Interrupt | Signal sent by hardware devices to get CPU attention. | Printer ready, disk I/O complete. |
| Maskable Interrupt | Can be ignored or delayed by the CPU using interrupt masks. | Timer interrupt in OS, peripheral device signals. |
| Non-Maskable Interrupt | Cannot be ignored, must be processed immediately. | Memory parity error, hardware failure signals. |
Q: In context of software engineering, UML stands for:
Utility Modern Laboratory
Unit Markup List
Unified Modeling Language
Unified Markup Link
[ Option C ]
UML stands for Unified Modeling Language, a standardized visual language used to model, design, and document software systems.
| UML DIAGRAM | TYPE | DESCRIPTION |
|---|---|---|
| Use Case Diagram | Behavioral | Represents the functional requirements of a system. It shows how users or external actors interact with the system to achieve specific goals. |
| Timing Diagram | Represents the behavior of objects over time, showing changes in state or conditions with respect to time. It is mainly used in real-time and embedded systems. | |
| Sequence Diagram | Illustrates how objects interact with each other in a time sequence. It shows the order of messages exchanged during a particular process. | |
| Activity Diagram | Models the flow of control or data from one activity to another. It is used to represent workflows and business processes. | |
| State Machine Diagram | Represents the different states of an object and the transitions between those states based on events. It is useful for modeling reactive systems. | |
| Component Diagram | Structural | Displays the organization and dependencies among various software components. It helps in understanding the implementation structure of the system. |
| Deployment Diagram | Describes the physical architecture of the system, showing hardware nodes and the software components deployed on them. | |
| Class Diagram | Describes the static structure of a system by showing classes, their attributes, operations, and the relationships among them. | |
| Object Diagram | Provides a snapshot of instances of classes (objects) and their relationships at a particular moment in time. It helps in understanding the system’s runtime behavior. | |
| Package Diagram | Groups related classes or elements into packages and shows dependencies among these packages. It helps in managing large-scale systems. | |
| Composite Structure Diagram | Shows the internal structure of a class and the collaborations among its parts. It helps in analyzing complex system components. |
Q: A block of addresses is granted to a small organization. We know that one of the addresses is 205.16.37.39/28. What is the last address in the block?
205.16.37.32
205.16.37.47
205.16.37.39
205.16.37.0
[ Option B ]
When an IP address is written with CIDR notation, such as 205.16.37.39/28, it tells us that the first 28 bits represent the network part, and the remaining 4 bits represent the host part of the address.
Since 4 bits are reserved for hosts, the total number of addresses in this subnet is 24=16. These addresses include both the network address and the broadcast address.
To find the exact block range, we must identify where the given IP (205.16.37.39) falls. Subnets with a /28 prefix have a block size of 16, and the subnets start at multiples of 16 in the last octet. Thus, the valid subnet ranges in the fourth octet are 0–15, 16–31, 32–47, 48–63, and so on. The number 39 lies between 32 and 47, which means the network address is 205.16.37.32.
Since the subnet contains 16 addresses, they run sequentially from 205.16.37.32 to 205.16.37.47. The first address 205.16.37.32 is reserved as the network address, and the last address 205.16.37.47 is reserved as the broadcast address for this subnet.
| PROPERTY | VALUE |
|---|---|
| Given IP | 205.16.37.39/28 |
| Subnet Mask | 255.255.255.240 |
| Network Address | 205.16.37.32 |
| First Usable Host | 205.16.37.33 |
| Last Usable Host | 205.16.37.46 |
| Broadcast Address | 205.16.37.47 |
Q: Which of the following is not true for relation S defined on set R of real numbers?
(x, y) ∈ S ⇔ |x| - |y| ≤ 1 is reflexive but not symmetric.
(x, y) ∈ S ⇔ |x − y| ≤ 1 is reflexive and symmetric.
(x, y) ∈ S ⇔ 0 < |x − y| ≤ 1 is symmetric and transitive.
(x, y) ∈ S ⇔ 0 < |x| – |y| ≤ 1 is neither symmetric nor transitive.
[ Option C ]
Q: Which of these supports compile-time polymorphism in C++?
Templates
Inheritance
Abstract Classes
Virtual Functions
[ Option A ]
Compile-time polymorphism in C++ means the decision about which function to invoke is made during compilation, not at runtime. There are two main features in C++ that support compile-time polymorphism:
Templates enable generic programming, where functions or classes can work with different data types without being rewritten. The compiler generates code at compile-time for each data type used, which is compile-time polymorphism.
Q: In which of the following system development types agile methods have been very successful?
Waterfall model-based development where a company is developing a small or medium-sized hardware for sale.
Custom system development within an organization, where there is no commitment from the customer to become involved in the development process and where there are a lot of external rules and regulations that affect the software.
Product development where a software company is developing a small or medium-sized product for sale.
Product development where a software company is developing a large size product for sale.
[ Option C ]
Agile is a software development methodology that emphasizes iterative development, flexibility, and customer collaboration. Unlike traditional methods like the Waterfall Model, where all requirements are defined upfront and changes are costly, agile allows teams to deliver software in small increments, gather continuous feedback, and adapt to changing requirements.
Agile works best in situations where requirements are not fully known at the start, projects are small to medium in size, and frequent customer involvement is possible.
In contrast, Waterfall is more suitable for projects that are large, heavily regulated, or hardware-oriented, where sequential and structured development is necessary.
| CRITERIA | AGILE | WATERFALL |
|---|---|---|
| Project Size | Small to medium. | Medium to large. |
| Requirements | Flexible / changing. | Well-defined / stable. |
| Customer Involvement | High, continuous feedback. | Low, usually at start and end. |
| Regulatory Constraints | Low to moderate. | High. |
| Development Approach | Iterative or incremental. | Sequential or phase-based. |
| Best Suited For | Small or medium software product. | Hardware projects, large-scale enterprise systems. |
| Adaptability to Change | Very high. | Low. |
| Delivery | Frequent releases / increments. | Single final release. |
Q: What is an adhoc network as per IEEE 802.11?
A basic service set without an access point.
A basic service set with an access point.
Two or more basic service sets with access point.
Only access points but no basic service set.
[ Option A ]
In wireless networking, IEEE 802.11 is the standard that defines Wi-Fi networks. Under this standard, a Basic Service Set (BSS) is the fundamental building block of a wireless LAN. There are two primary types of network configurations:
Infrastructure Mode : This setup includes a central Access Point (AP) that coordinates communication between wireless devices (stations). Multiple BSS can be interconnected via access points.
Ad hoc Mode (Independent Basic Service Set (IBSS)) :This setup does not have an access point. Wireless devices communicate directly with each other, forming a temporary or decentralized network.
Ad hoc networks are typically used for small, temporary networks where no central infrastructure exists, like in Peer-to-Peer connections.
Q: The memory allocation technique used in paging may have:
External fragmentation
Internal fragmentation
Hybrid fragmentation
No fragmentation
[ Option B ]
Paging is a memory management technique that divides physical memory into fixed-size blocks called frames and logical memory into blocks of the same size called pages. Pages are mapped to frames using a page table, allowing non-contiguous allocation of memory.
| TYPE OF FRAGMENTATION | DESCRIPTION |
|---|---|
| Internal Fragmentation. | Occurs when the last allocated page/frame is not fully used. Wasted memory inside allocated blocks due to fixed-size allocation. Paging may cause internal fragmentation because the last page of a process might not be completely filled. |
| External Fragmentation. | Occurs when there is enough total memory to satisfy a request, but it is not contiguous. Wasted memory outside allocated blocks due to scattered free memory. |
Q: Which of the following is not a part of Rational Unified Process (RUP) that is a part of modern process model?
Elaboration
Exception
Construction
Transition
[ Option B ]
The Rational Unified Process (RUP) is a widely used modern software process model that organizes software development into a series of phases to improve control, predictability, and quality. RUP defines four main phases:
Q: GSM technology is combination of _____________.
TDMA and FDMA
TDMA and CDMA
CDMA and FDMA
TDMA, CDMA and FDMA
[ Option A ]
GSM (Global System for Mobile Communications) is a digital cellular technology that combines multiple access techniques to efficiently use the available radio spectrum.
GSM uses Frequency Division Multiple Access (FDMA) to divide the available frequency bands into separate channels, and Time Division Multiple Access (TDMA) to divide each frequency channel into time slots that can be shared by multiple users.
Q: Which of the following best describes memorization in dynamic programming?
Storing the results of function calls to avoid recomputation
Rewriting recursive functions to be iterative
Ignoring sub-problems that don’t affect the final result
Using arrays to sort sub-problems
[ Option A ]
Memorization is a key technique used in dynamic programming to improve efficiency by:
In other word, instead of recalculating the result every time, we "memorize" (store) it — typically using an array, map, or hash table.
Q: What will be the output of the following program?
#include<iostream>
using namespace std;
class base {
public:
virtual void fun() {
cout<<”base::fun”<<endl;}
};
class derived : public base {
public:
void fun() {
cout<<”derived::fun”<<endl;}
};
int main() {
derived t1;
base *t2=new derived();
base *t3=&t1;
t2->fun();
t3->fun();
return 0;
}
base::fun
derived::fun
derived::fun
derived::fun
derived::fun
base::fun
base::fun
base::fun
[ Option B ]
Here, fun() in the base class is virtual, which means if a base class pointer points to a derived class object, the derived class function will be called.
Q: If a graph has 31 edges and each vertex of the graph has degree atleast 3, then maximum number of possible vertices in the graph is
19
20
21
22
[ Option B ]
We use the Handshaking Theorem, which states that the sum of the degrees of all vertices in an undirected graph equals twice the number of edges:
Sum of degrees of all vertices=2×Number of edges
Here, E=31. So,
Sum of degrees = Sum of degrees=2×31=62
The given condition is that each vertex has degree at least 3. Now, let the number of vertices be n. Then, Sum of degrees ≥ 3n. We already know the exact sum is 62, so, 3n ≤ 62.
Finally solve for n, n ≤ 62/3 = 20.66. Since the number of vertices must be an integer, the maximum possible number of vertices is 20.
Q: Given the overloaded functions:
int max (int a, int b);
double max (double a, double b);
What will be the output of the following code? (Assume no syntax errors)
double val = 6.8;
double result = max (2.3, val);
Calls double max (double, double)
Compilation error due to ambiguity
9.1
Calls int max(int,int)
[ Option A ]
C++ resolves function overloading based on the exact match of argument types. In this case, max(2.3, 6.8) passes two double values, so the compiler selects the function double max(double a, double b). Since the argument types match exactly, there is no ambiguity or type conversion required.
Q: Consider a disk queue with requests for Input/Output to blocks on cylinders in the given order. The disk head is initially at cylinder 53.
98, 183, 37, 122, 14, 124, 65, 67
What will be the number of total head movement for SSTF and SCAN algorithms respectively?
236, 208
208, 236
208, 208
236, 236
[ Option A ]
Disk scheduling algorithms decide the order in which I/O requests are serviced to minimize disk head movement. Two common algorithms are:
SSTF (Shortest Seek Time First):
SCAN (Elevator Algorithm):
Q: Which of the following is NOT a characteristic of RAID?
RAID is a set of physical disk drives viewed by the OS as a single logical drive.
Data are distributed across physical drives of an array in a scheme known as striping.
Redundant disk capacity is used to stores parity information, which guaranteeing data recoverability in case of disk failure.
RAID is primarily used to compress and encrypt data across multiple disks.
[ Option D ]
RAID is a storage technology that combines multiple physical disks into a single logical unit to improve performance and reliability (fault tolerance). Key characteristics of RAID include:
Q: Input block size, key size and output block size in Data Encryption Standard (DES) are respectively:
128-bit, 64-bit, 128-bit
64-bit, 32-bit, 64-bit
64-bit, 56-bit, 64-bit
64-bit, 64-bit, 128-bit
[ Option C ]
Data Encryption Standard (DES) is a symmetric key block cipher widely used for secure data transmission.
This design allows secure encryption and decryption using the same 56-bit key.
| Symmetric Encryption Algorithms | Key Size | Message Size |
|---|---|---|
| DES (Data Encryption Standard) | 56 bits | 64-bit block |
| 3DES (Triple DES) | 112 or 168 bits | 64-bit block |
| AES (Advanced Encryption Standard) | 128, 192, or 256 bits | 128-bit block |
| Blowfish | 32–448 bits | 64-bit block |
| IDEA (International Data Encryption Algorithm) | 128 bits | 64-bit block |
| RC4 | 40–2048 bits | Stream cipher |
| Asymmetric Encryption Algorithms | Key Size | Message Size |
|---|---|---|
| RSA (Rivest–Shamir–Adleman) | 1024–4096 bits | Variable |
| ECC (Elliptic Curve Cryptography) | 160–521 bits | Variable |
Q:
Match the virtual memory terminologies in Column I to their descriptions in Column II:
| Column I | Column II |
|---|---|
| a. Virtual address | i. The virtual storage assigned to a process. |
| b. Virtual address space | ii. The range of memory addresses available to a process. |
| c. Address space | iii. The address of a storage location in main memory. |
| d. Real address | iv. The address assigned to a location in virtual memory to allow that location to be accessed as though it were part of main memory. |
Choose the correct option:
a – ii, b – i, c – iii, d – iv
a – iv, b – i, c – ii, d – iii
a – i, b – iii, c – ii, d – iv
a – iv, b – iii, c – i, d – ii
[ Option B ]
Virtual Memory is a memory management technique that gives an application the illusion of having a large, continuous block of memory, even though it may be physically fragmented or partially stored on disk.
| TERM | DESCRIPTION |
|---|---|
| Virtual Address | A virtual address is the address assigned to a location in virtual memory. It allows the CPU to access data as if it were in the main memory. |
| Virtual Address Space | This refers to the total virtual storage assigned to a process. It represents the range of virtual addresses a process can use. |
| Address Space | The address space defines the range of memory addresses available to a process (virtual or physical). |
| Real Address | The real address (also called physical address) refers to the actual location in the main memory (RAM). |
Q: Which of the following statements cannot be proved by principle of mathematical induction?
6n+2 + 72n+1 is divisible by 43
└n ≥ 2n-1
If a and b are odd integers, then (a + b) is an even integer
For n ≥ 4, 3n > n3
[ Option C ]
Q: In context of a relational database, choose a false statement :
A super key is not always a candidate key.
A minimal super key is called a candidate key.
One of the candidate keys is designated as primary key.
Primary key is a proper subset of one of the candidate keys.
[ Option D ]
In a relational database, a Super Key is any set of attributes that uniquely identifies tuples, but it may contain extra attributes and hence is not always minimal.
A Candidate Key is a minimal super key, meaning no subset of it can be a super key. Among candidate keys, one is chosen as the Primary Key to uniquely identify tuples.
Since the Primary Key itself is a candidate key, it cannot be a proper subset of another candidate key.
| KEY TYPE | DESCRIPTION |
|---|---|
| Super Key | A set of one or more attributes that uniquely identifies a tuple in a relation. It may contain extra attributes. |
| Candidate Key | A minimal super key, i.e., a super key with no unnecessary attributes. Each relation can have one or more candidate keys. |
| Primary Key | A candidate key chosen by the database designer to uniquely identify tuples in a relation. Must not contain NULL. |
| Alternate Key | Any candidate key that is not selected as the primary key. |
| Foreign Key | An attribute in one table that refers to the primary key of another table to maintain referential integrity. |
| Composite Key | A key that consists of two or more attributes to uniquely identify a tuple. |
| Partial Key | Used in weak entity sets to uniquely identify tuples only when combined with the primary key of the identifying entity. |
Q: For positive n, solution to recurrence relation T(n)=T(2n/3)+1 is:
Ө(lg n)
Ө(n lg n)
Ө(n!)
Ө(n)
[ Option A ]
Q: Given functional dependencies on U(P, Q, R, S, T):
P → QR
RS → T
Which dependencies cannot be inferred?
P → R
PS → T
R → T
PS → Q
[ Option C ]
To see which dependencies follow from the given ones, compute attribute closures using the given FDs: P→QR and RS→T. If an attribute set’s closure contains the right-hand side, that dependency is implied.
(a)
P→R
Find P+ :
P+ = {P}
P+={P,Q,R} Using P→QR
R is in P+ ⇒ P→R inferred.
(b)
PS → T
Find PS+ :
(PS)+={P,S}
(PS)+={P,S,Q,R} Using P → QR
Now, (PS)+ has RS so Using RS→T
(PS)+={P,S,Q,R,T}
T is in (PS)+ ⇒ PS → T inferred.
(c)
R→T
Find R+ :
R+ = {R}
No dependency with just R, so cannot go further.
T is not in R+ ⇒ R→T cannot be inferred.
(d)
PS → Q
Find PS+ :
(PS)+ = {P,S)
(PS)+ = {P,S,Q,R) Using P→QR
Now, (PS)+ has RS so Using RS→T
(PS)+={P,S,Q,R,T}
Q is in (PS)+ ⇒ PS → Q inferred.
Q: In the context of text normalization, which of the following statements best describes lemmatization?
It is the process of converting all letters in a text to lowercase.
It is the process of splitting a paragraph into words.
It maps different word forms to their base or root form.
It removes all punctuation marks from the text.
[ Option C ]
In text normalization, Lemmatization reduces words to their base or dictionary form. For instance, words like “better”, “best”, and “good” can all be lemmatized to “good”, depending on context. Similarly, “studying”, “studies”, and “studied” are mapped to “study”. This process helps in natural language processing by treating different forms of the same word as a single entity.
Q: Best case time complexity of quick sort is achieved when?
All elements are the same
Array is sorted
Pivot is always the first element
The pivot divides the array equally in every position
[ Option D ]
The best-case time complexity of Quick Sort occurs when the pivot divides the array into two equal halves at every recursive step.
| Case | Time Complexity |
|---|---|
| Best | O(n log n) |
| Average | O(n log n) |
| Worst | O(n2) |
Q: Consider the following and determine what will be printed?
#include<iostream>
using namespace std;
void Xhandler(int test)
{
try {
if (test) throw test;
}
catch (int i) {
cout<<”Hello# : “<<i<<”\n”;
}
}
int main()
{
Xhandler(1);
Xhandler(0);
Xhandler(3);
Xhandler(2);
return 0;
}
Hello# : 1
Hello# : 0
Hello# : 3
Hello# : 2
Hello# : 1
Hello# : 3
Hello# : 2
Hello# : 1
Hello# : 3
Hello# : 2
Hello# : 0
Hello# : 1
Hello# : 2
Hello# : 3
[ Option B ]
The function Xhandler(int test) checks if test is non-zero. If test is non-zero, it throws test as an exception. The catch (int i) block catches the integer exception and prints "Hello# : " followed by the value of i. If test is zero, no exception is thrown, so nothing is printed.
In main():
Q: Which of the following, best represents an event to invoke medium-term scheduler?
Clock interrupts
I/O interrupts
New process creation
Need of swapping
[ Option D ]
In an Operating System, the CPU scheduling process involves three levels of schedulers:
Q: An IPv4 datagram arrives with the following Header values: In Fragment Offset and Flag field respectively Fragment Offset = 0, MF = 0. What does this imply?
The packet was fragmented and this is the last fragment.
The packet is the first fragment of a fragmented datagram.
The packet was not fragmented at all.
The packet is a middle fragment.
[ Option C ]
In IPv4, when a packet is too large to be transmitted in one piece, it may be fragmented into smaller packets. Each fragment carries two important fields:
If a packet has Fragment Offset = 0 and MF = 0, it means that there are no fragments before or after it. A Fragment Offset of 0 shows it is the first fragment, but since MF = 0 indicates no more fragments, the packet must be unfragmented and sent as a single complete datagram.
Q: In a system with a 32-bit logical address space and a page size of 4 KB approximately, how many entries are there in the page table?
220 entries
210 entries
232 entries
212 entries
[ Option A ]
In a paging system, the logical address space is divided into fixed-size pages, and a page table maps each logical page to a physical frame in memory. In this problem, the system has a 32-bit logical address space, which means it can address 232 bytes.
The page size is given as 4 KB, which is 212 bytes. To find the number of pages, we divide the total logical address space by the page size: 232/ 212=220.
Since each page requires one entry in the page table, the page table will contain 220 entries.
Q: In digital modulation schemes using two carriers, a constellation diagram is particularly useful because it helps to
Measure only the frequency variations in the signal.
Visualize the amplitude and phase of each signal element.
Encode binary data directly without modulation.
Eliminate noise from the transmitted signal.
[ Option B ]
In digital communication, Modulation is the process of varying a carrier signal (sine wave) to transmit data. Digital modulation schemes often use two or more carriers, which can vary in amplitude, phase, or frequency to represent binary information.
A Constellation Diagram is a graphical representation of these modulated signals on a 2D plane, where the x-axis represents the in-phase component (I) and the y-axis represents the quadrature component (Q). Each point in the diagram corresponds to a unique amplitude and phase combination, allowing engineers to visualize the transmitted symbols and detect errors.
| TOOL | PURPOSE | OBSERVED PARAMETERS |
|---|---|---|
| Constellation Diagram | Visualization of digital modulation. | Amplitude and Phase. |
| Eye Diagram | Time-domain signal analysis. | Signal timing, Jitter, ISI. |
| Spectrum Analyzer | Frequency analysis. | Frequency, bandwidth, harmonics. |
Q: The output of the following statements are
int a=5;
cout<<"FIRST"<<(a<<2)<<"SECOND";
FIRST20SECOND
SECOND25FIRST
SECOND8FIRST
FIRST52SECOND
[ Option A ]
In C++, the symbol << is used in two ways: it works as an output operator (also called the insertion or put-to operator) when used with cout, and as a bitwise left shift operator when it appears between two numeric values.
A bitwise left shift moves the bits of a number to the left by a certain number of positions. In the statement cout << "FIRST" << (a << 2) << "SECOND";, the part (a << 2) is calculated like this, since a = 5, its binary form is 0000 0101. When we shift the bits two places to the left, it becomes 0001 0100, which equals 20 in decimal. So, (a << 2) gives the value 20.
Finally, when substituted into the output statement, it becomes cout << "FIRST" << 20 << "SECOND";, which displays the text FIRST20SECOND on the screen. Note that there are no spaces unless explicitly added.
Q: Which of the following statements about destructors in C++ is TRUE?
A destructor must have a return type, typically void.
A destructor can take parameters to customize object cleanup.
If a class does not define a destructor, the compiler provides a default public destructor.
Destructors can be overloaded if needed.
[ Option C ]
Q: A linear list in which elements can be added or removed at either end but not in the middle, is called ___________.
Priority Queue
Threaded Binary Tree
Dequeue
Linked List
[ Option C ]
A Dequeue stands for Double Ended Queue. It is a linear data structure where:
In priority queue, elements are inserted in any order but removed based on priority, not position.
The threaded binary tree is type of binary tree optimized for in-order traversal, not a linear list.
The linked list allows insertions and deletions at any position, including the middle.
Q: A drawer contains 12 red and 12 blue socks. All socks are unmatched. To get at least two blue socks, how many socks must be taken out at random without replacement?
24
18
14
12
[ Option C ]
A drawer contains 12 red and 12 blue socks, all unmatched. To ensure at least 2 blue socks are drawn, we consider the worst-case scenario, where all red socks are drawn first. There are 12 red socks, so after drawing all of them, we still have 0 blue socks.
The next two socks drawn must be blue since only blue socks remain. Therefore, the total number of socks that must be drawn to guarantee at least 2 blue socks is 12 (all red) + 2 (blue) = 14.
Q: Given below are statements in context of Armstrong's axioms to find logically implied functional dependencies in DBMS.
I. If B→C holds and A is a set of attributes, then AB → AC holds.
II. If A is a set of attributes and B ⊆ A, then A → B holds.
Choose the correct ordered pair to complete the following sentence.
“Statement I is called __________ rule and Statement II is called __________ rule.”
Reflexivity, Augmentation
Augmentation, Reflexivity
Augmentation, Transitivity
Transitivity, Augmentation
[ Option B ]
Armstrong’s Axioms are a set of inference rules used to derive all functional dependencies (FDs) logically implied by a given set of FDs in a database.
Statement I says that if a functional dependency B → C holds, then adding the same set of attributes A to both sides results in AB → AC. This is known as the Augmentation Rule. Statement II says that if B ⊆ A (B is a subset of A), then A → B always holds, which is called the Reflexivity Rule.
| Axiom / Rule | Description | Example |
|---|---|---|
| Reflexivity | If B ⊆ A, then A → B. A set of attributes functionally determines any of its subsets. | If A = {X, Y} and B = {X}, then {X, Y} → {X} |
| Augmentation | If A → B holds, and C is a set of attributes, then AC → BC also holds. Adding same attributes to both sides preserves the dependency. | If A → B and C = {Z}, then AZ → BZ |
| Transitivity | If A → B and B → C, then A → C. Functional dependencies can be combined through an intermediate attribute. | If A → B and B → C, then A → C |
| Union | If A → B and A → C, then A → BC. Dependencies from the same determinant can be combined. | If A → B and A → C, then A → BC |
| Decomposition | If A → BC, then A → B and A → C. A dependency on multiple attributes can be split into separate dependencies. | If A → BC, then A → B and A → C |
| Pseudo Transitivity | If A → B and BC → D, then AC → D. Combines transitivity with augmentation. | If A → B and BC → D, then AC → D |
Q: Consider the following code and determine the output:
#include<iostream>
using namespace std;
class A
{
public:
virtual void vfunc() {
cout<<”This is A’s vfunc()\n”;
}
};
class B : public A
{
public:
void vfunc() {
cout<<”This is B’s vfunc()\n”;
}
};
class C : public A
{
public:
void vfunc() {
cout<<”This is C’s vfunc()\n”;
}
};
int main()
{
A *p, b;
B d1;
C d2;
p=&d1;
p->vfunc();
p=&b;
p->vfunc();
p=&d2;
p->vfunc();
return 0;
}
This is A’s vfunc()
This is B’s vfunc()
This is C’s vfunc()
This is C’s vfunc()
This is A’s vfunc()
This is B’s vfunc()
This is A’s vfunc()
This is C’s vfunc()
This is B’s vfunc()
This is B’s vfunc()
This is A’s vfunc()
This is C’s vfunc()
[ Option D ]
In class A, vfunc() is declared as virtual, which means that when this function is called through a base class pointer, the function of the actual object type will be executed. This concept is called Runtime Polymorphism.
Q: Complete the code for overloaded template by replacing the ABCD:
#include<iostream>
using namespace std;
template <class X>
void f (X a)
{
cout<<”Inside ”;
}
ABCD
{
cout<<”Outside ”;
}
int main()
{
f (10);
f (10,20);
return 0;
}
template void f (X a, Y b)
<class X, class Y>
template <class X, class Y>
template f (X a, Y b)
template <class X, class Y>
void f (X a, Y b)
[ Option D ]
The original function template is declared for one argument as:
template <class X>
void f(X a) {
cout << "Inside\n";
}
In main(), the code calls:
f(10); // Calls the first template function.
f(10, 20); // Needs a new template function for two arguments.
The second call f(10, 20) cannot use the first template because it only takes one argument. Therefore, we need to overload the template for two arguments of possibly different types as:
template <class X, class Y>
void f(X a, Y b) {
cout << "Outside\n";
}
Q: Correct order of database abstraction levels, from the highest level of abstraction to the lowest level of abstraction is:
Physical level, View level, Logical level
View level, Logical level, Physical level
Physical level, Logical level, View level
Logical level, Physical level, View leve
[ Option B ]
In a database management system, the three levels of data abstraction are organized to simplify data management and improve security.
| ABSTRACTION LEVEL | DESCRIPTION | PURPOSE |
|---|---|---|
| View Level | Highest level of abstraction. It shows how users interact with data through customized views that hide complexity. | Used by end users and application programs to access only relevant data. |
| Logical Level | Describes what data is stored in the database and relationships among them. Defines schema, tables, fields, and constraints. | Used by database designers and DBAs to design overall database structure. |
| Physical Level | Lowest level of abstraction. It describes how data is physically stored on disk (files, blocks, indexes). | Used by system administrators and DBMS software to optimize performance and storage. |
Q: Let V = {a, b, c, d, e} is set of vertices and E = {(ab), (ae), (bc), (cd), (de)} is set of edges of a directed graph G = (V, E). which of the following is a valid topological ordering of G?
a, d, e, b, c
e, d, c, b, a
a, b, c, d, e
a, b, e, c, d
[ Option C ]
Topological sorting is possible only for Directed Acyclic Graphs (DAGs). A topological order is a linear ordering of vertices such that for every directed edge (u → v), u comes before v.
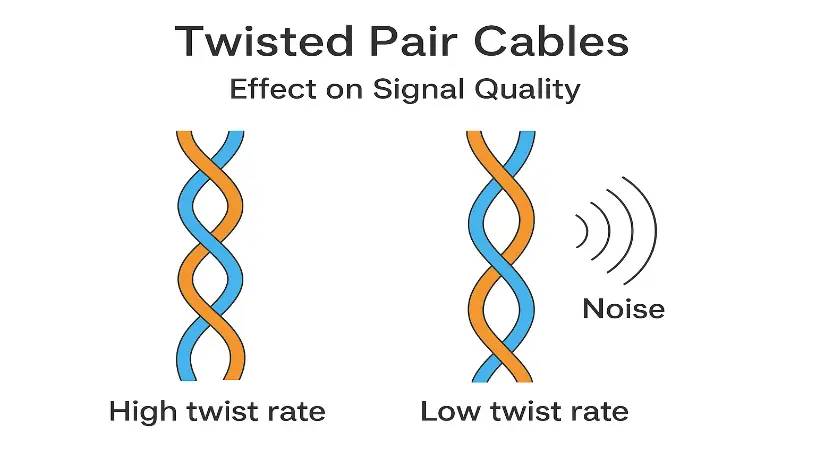
Q: Which of the following statements about twists in twisted pair cables is TRUE?
Increasing the number of twists per unit of length reduces the cable's electrical resistance.
More twists per unit of length in the cable increase signal distortion.
A higher twist rate gives better signal quality.
Fewer twists per unit of length in the cable result in better noise immunity.
[ Option C ]
Twisted pair cables are a type of electrical cable commonly used in networking and telecommunications.
Twisted pair cables consist of two insulated copper conductors twisted together to reduce electromagnetic interference (EMI) and crosstalk between adjacent pairs and improves overall signal quality.
Q: Which of the following is not a part of the four activities that are fundamental to software engineering?
Software Specification
Software Design and Implementation
Software Evolution
Software Cohesion
[ Option D ]
In Software Engineering, there are four fundamental activities that guide the development and maintenance of software systems.
| ACTIVITY | MEANING |
|---|---|
| Software Specification | Defining what the software should do and the requirements it must satisfy. |
| Software Design and Implementation | Designing the system architecture and writing the actual code to implement the design. |
| Software Validation | Ensuring that the software meets the specified requirements and works correctly. |
| Software Evolution | Modifying and updating software to adapt to changing requirements or fix defects after deployment. |
Q: If 2n words are in main memory and 2K words are in cache memory, then the bits for tag field and index field of a n-bit memory address are respectively,
n, K
K, n
n−K, K
n+K, n
[ Option C ]
In Cache Memory, a main memory address is divided into tag, index, and block offset fields if using Direct Mapping.
If main memory has 2n words and cache has 2K words, then:
Index field = K bits (To select one of 2K cache lines)
Tag field = n−K bits (Remaining bits to identify the memory block)
Q: If the number of elements in sets A and B be 5 and 2 respectively, then the number of subsets of A × B, such that each subset has at least 3 and at most 6 elements, is
892
672
792
540
[ Option C ]
The Cartesian product A×B has |A| × |B| = 5 × 2 = 10 elements. To find the number of subsets with at least 3 and at most 6 elements, we calculate the number of subsets of size 3, 4, 5, and 6. Using the combination formula, we have C(10,3) = 120, C(10,4) = 210, C(10,5) = 252, and C(10,6) = 210. Adding these gives 120 + 210 + 252 + 210 = 792. Therefore, there are 792 subsets of A × B with 3 to 6 elements.
Q: Which type of semaphore can be used to provide mutual exclusion when mutex locks are not available?
Counting semaphore
Binary semaphore
Timed semaphore
Spinlock
[ Option B ]
Semaphore is a synchronization tool used to control access to shared resources in concurrent systems. There are two types of semaphores:
Mutex locks are specialized locks for mutual exclusion, but if they are not available, a binary semaphore can perform the same function.
Q: Let QUSVPTR is in-order traversal and UVSQTRP is post-order traversal of a binary tree T. Which of the following is pre-order traversal of the binary tree T?
PUQSVRT
UVRTPQS
SQPRTVU
PQSUVRT
[ Option D ]
Q: Which of the following statements correctly differentiates strict two-phase locking from rigorous two-phase locking?
In strict 2PL, exclusive locks are released at the end of the transaction; in rigorous 2PL, all locks (shared and exclusive) are released at the end of the transaction.
In strict 2PL, all locks are released immediately after use; in rigorous 2PL, locks are never released.
Strict 2PL ensures serializability and deadlock freedom.
Rigorous 2PL ensures serializability and deadlock freedom.
[ Option A ]
Two-Phase Locking (2PL) is a concurrency control protocol used in databases to ensure serializability of transactions.
Strict 2PL and Rigorous 2PL are two variants of the two-phase locking protocol. In strict 2PL, only exclusive locks are held until the transaction commits, while shared locks can be released earlier.
In rigorous 2PL, all locks, both shared and exclusive are held until the end of the transaction. This makes rigorous 2PL stricter and ensures that no other transaction can access any locked data until the current transaction completes, providing serializability and strictness.
Q: Which of the following statements is TRUE about the High-Level Data-Link Control (HDLC) protocol?
HDLC is a character-oriented protocol used on asynchronous links.
HDLC provides authentication mechanisms for secure communication.
HDLC is a point-to-point, bit-oriented protocol standardized by ISO.
HDLC is used exclusively for wireless communication between wireless nodes.
[ Option C ]
HDLC (High-Level Data Link Control) is a Layer-2 (Data Link Layer), bit-oriented (it treats the transmitted data as a stream of bits) protocol formalized by ISO. It supports reliable framing, Error Detection (CRC) for reliable communication and operates commonly in point-to-point links (Router-to-Router).
| PROTOCOL | TYPE | MEDIUM | ORIENTATION |
|---|---|---|---|
| HDLC | Data Link | Point-to-point / multipoint | Bit-Oriented. |
| BISYNC (Binary Synchronous Communication) | Data Link | Synchronous | Character-Oriented. |
| PPP (Point-to-Point Protocol) | Data Link | Point-to-point | Byte-Oriented. |
Q: We want to add to the relation Studio(name, address, president), all movie studios that are mentioned in the relation Movie(title, year, length, incolour, studioName, producer) but do not appear in Studio. What will be the correct query for this?
INSERT INTO Studio(name) SELECT DISTINCT studioName FROM Movie WHERE studioName NOT IN (SELECT name FROM Studio);
INSERT INTO Studio(name) values as SELECT DISTINCT studioName FROM Movie WHERE studioName NOT IN (SELECT name FROM Studio);
INSERT INTO Studio SELECT DISTINCT studioName FROM Movie WHERE studioName NOT IN (SELECT name FROM Studio);
INSERT INTO Studio(name) values SELECT DISTINCT studioName FROM Movie WHERE studioName NOT IN (SELECT name FROM Studio);
[ Option A ]
The goal is to insert into the Studio table the names of all studios that appear in the Movie relation but are not already present in Studio.
To insert into the relation Studio all studios that appear in the Movie relation but are not already present, we use the INSERT INTO ... SELECT statement. The correct query is:
INSERT INTO Studio(name)
SELECT DISTINCT studioName
FROM Movie
WHERE studioName NOT IN (SELECT name FROM Studio);
This query selects all unique studio names from the Movie table and inserts them into the Studio table, but only if they do not already exist in Studio. The DISTINCT keyword ensures that duplicate names are not inserted, and the NOT IN condition prevents inserting studios already present.
Q: Choose the correct option considering the assertion and reason in context of Service Level Agreement (SLA) in cloud computing.
Assertion (A): SLAs are important only from the customer's point of view.
Reason (R): Customers use SLAs to compare services and choose the best CSP.
Both (A) and (R) are true, and (R) is the correct explanation of (A).
Both (A) and (R) are true, but (R) is not the correct explanation of (A).
(A) is true, but (R) is false.
(A) is false, (R) is true.
[ Option D ]
A Service Level Agreement (SLA) is a contract between a cloud provider and a customer that defines expected service quality, availability, and responsibilities. SLAs are important for both the customer, who uses them to compare and choose services, and the provider, who clarifies obligations and limits liability.
Q: Consider Column – I and Column – II in context of malwares.
| Column – I | Column – II |
|---|---|
| a. Rootkit | i. An infected machine activated to launch attacks on other machines. |
| b. Zombie | ii. Appears to be useful, but also has a hidden malicious function. |
| c. Spyware | iii. Collects information and transmits it to another system. |
| d. Trojan Horse | iv. Set of hacker tools used after breaking into a computer system and gaining root-level access. |
Which of the following is the most suitable match of Column – I and Column – II?
a – iv, b – i, c – iii, d – ii
a – ii, b – iii, c – iv, d – i
a – ii, b – i, c – iii, d – iv
a – i, b – iv, c – ii, d – iii
[ Option A ]
| Malware Type | Description |
|---|---|
| Virus | Infects files and programs, spreads when infected files are shared or executed. |
| Worm | Self-replicating malware that spreads across networks without user action. |
| Trojan Horse | Appears as legitimate (genuine) software but secretly creates backdoors or installs malware. |
| Rootkit | Hides deep in the OS, modifies system functions, and gives attackers administrator control. In other word, set of hacker tools installed after gaining root-level access to a system, allowing attackers to hide their presence and control the system. |
| Spyware | Monitors user activities, stealing data such as browsing history, keystrokes, and credentials. |
| Ransomware | Encrypts files and demands payment for the decryption key. |
| Zombie | An infected machine that can be remotely controlled to launch attacks, often as part of a botnet. |
| Adware | Displays intrusive advertisements, often bundled with free software. |
| Keylogger | Records user keystrokes to steal sensitive information like passwords and credit card details. |
Q: In the context of mobile computing, GSM stands for:
Global System for Mobile Communications
Global Positioning System for Mobile phones
Guaranteed Security for Mobility
Graded protocol for Safety Management
[ Option A ]
GSM stands for Global System for Mobile Communications. It was developed by ETSI (European Telecommunications Standards Institute) in the late 1980s. In the context of mobile computing, GSM is the widely adopted standard for cellular networks.
It defines the protocols for digital mobile communication, enabling voice calls, text messaging, and data transfer over mobile networks.
Q: A simple graph has
Both parallel edges and self-loops
Self-loops but not parallel edge
Parallel edges but no self-loop
Neither parallel edge nor self-loop
[ Option D ]
A Simple Graph is a type of graph that does not contain any parallel edges (multiple edges) or self-loops (an edge from a vertex to itself). Each edge in a simple graph connects two distinct vertices, and there can be at most one edge between any pair of vertices.
Q: Which of the following describes a 32 X 8 ROM?
8 words of 32 bits each
32 words of 8 bits each
32 input lines and 8 output lines
8 input lines and 32 output lines
[ Option B ]
A Read Only Memory (ROM) is a type of non-volatile memory used to store data permanently. The notation “m × n” in memory terminology means that the ROM contains m words, and each word consists of n bits.
In a 32 × 8 ROM, there are 32 memory locations, and each location can store 8 bits of data. This means the ROM can store a total of 32×8=256 bits of information. Hence, a 32 × 8 ROM is best described as “32 words of 8 bits each.”
Q: Which of the following is not a valid heuristic used in relational query optimization?
Perform selection operations as early as possible.
Apply projections early to reduce the number of columns.
Avoid Cartesian products whenever possible.
Apply projections as late as possible to retain all attributes.
[ Option D ]
In Relational Query Optimization, heuristics are used to reduce the size of intermediate results and improve efficiency. Standard heuristics include performing selection operations as early as possible, applying projections early to reduce columns, and avoiding Cartesian products.
Applying Projections Late is contrary to optimization principles because it increases the number of attributes in intermediate results, leading to higher computational cost.
Q: Consider a linear array A which records the number of cars sold every year from 1932. Let base address of A is 200 and each memory cell of A occupies 4 words. Then address of array element for the year 1965 is:
233
332
1965
2165
[ Option B ]
Array A stores number of cars sold each year starting from 1932 So, A[0] corresponds to year 1932 or lower bound of array is 1932.
Base address = 200
Each element occupies 4 words i.e., 4 Bytes.
We are asked to find the address of the element corresponding to year 1965 or find the address of index position 1965. So,
LOC (A[I])=Base(A) + (I-Lower Bound) * W
LOC (A[1965]) = 200 + (1965-1932)*4
LOC (A[1965]) = 200 + 33 * 4
LOC (A[1965]) = 200 + 132
LOC (A[1965]) = 332
Q: For Boolean function, f(A, B, C) = Σ m(0, 1, 3, 5) + Σ d(2, 7) , the minimized sum-of-product equation is : (using K-Map)
A' + C'
A' + B' + C'
A' . B' . C'
C + A'
[ Option D ]
Q: Consider the following C++ code:
#include<iostream>
int change (int &);
int main()
{
int a=1, b=2;
a=change(b);
cout<<a<<b;
return 0;
}
int change (int &x)
{
x=10;
return(11);
}Find output of the above code.
Run time error
112
1110
Compile time error
[ Option C ]
In this C++ program, the function change is defined to take an integer reference as its parameter (int &x). Passing by reference (call by reference) means any changes made to x inside the function will directly affect the original variable passed in.
Q: In a fuzzy inference system, the defuzzification step is used to:
Convert crisp input into fuzzy values
Generate fuzzy output from rules
Convert fuzzy output into a crisp value
Normalize the fuzzy sets
[ Option C ]
In a fuzzy inference system, defuzzification converts the fuzzy output from the rule evaluation into a single crisp value that can be used for decision-making or control.
Q: Which Register holds the address of the next instruction to be executed?
Instruction Register
Accumulator
Program Counter
Data Register
[ Option C ]
The Program Counter (PC) is a special register in the CPU that stores the address of the next instruction to fetch and execute from memory.
After fetching the current instruction, the PC increments to point to the next instruction’s address unless modified by a jump or branch instruction.
This allows the CPU to execute the sequence of instructions in order and supports control flow changes.
Q:
Consider the program below. What will be the output?
#include<iostream>
#include<string>
using namespace std;
class Sample {
string name;
public:
Sample() {
cout<<”s”<<” ”;
}
Sample (string s) : name (s) {
cout<<name<<” ”;
}
};
int main() {
Sample s1;
Sample *s2=new Sample (“s2”);
Sample *s3;
new Sample (“s4”);
return 0;
} s s2 s s4
s2 s s4
s s2 s4
s2 s4 s
[ Option C ]
The line Sample (string s) : name (s), is a parameterized constructor of the class Sample, and : name(s) is an example of a member initializer list in C++. It means that the data member name will be initialized with the value of s before the constructor body runs.
Q: According to the duality theorem, the dual of the Boolean expression A+0=A is:
A.0=0
A+1=A
A.A=A
A.1=A
[ Option D ]
Principle of Duality says, every algebraic expression remains valid if you interchange:
1) AND (·) with OR (+)
2) 0 with 1
In simple words, for every Boolean law or expression, there exists a dual expression that is also valid. E.g.:
1) A + 0 = A, its Dual is A . 1 = A
2) A + A =A, its Dual is A . A = A
3) A . 0 = 0, its Dual is A + 1 =1
Q: Host C initiates two HTTP sessions to server B using source ports 26145 and 7532. Meanwhile, Host A — choosing source port numbers independently of C — also uses 26145 as the source port for its HTTP session to B. How does Server B correctly distinguish between these connections for communication?
Server B identifies each session using only the destination port value.
Server B blocks sessions that reuse any source port across different hosts.
Server B uses all four fields: source IP, source port, destination IP, destination port.
Server B accepts only one connection and rejects the duplicate port requests.
[ Option C ]
In the TCP/IP protocol suite, each TCP connection is uniquely identified by a socket, which consists of four elements:
This combination is called a 4-Tuple. It ensures that even if multiple clients use the same source port number, or a single client opens multiple connections to the same server, the server can distinguish each connection uniquely.
Therefore, even though Host C and Host A both use source port 26145 to connect to Server B’s HTTP port, their source IPs differ, making the 4‑tuples unique. The server’s socket table tracks each connection by its 4‑tuple and can distinguish and route data correctly.
Q: Let a BST is constructed by inputting an ordered list [33, 45, 2, 91, 47, 95] from left to right. Which of the following pair of elements will be on the last level of the BST?
47, 91
47, 95
2, 95
91, 95
[ Option B ]
33
/ \
2 45
\
91
/ \
47 95
Q: Consider two processes, P3 and P4, that share global variables b and c, with initial values b = 1 and c = 2. At some point in its execution, P3 executes the assignment b = b + c, and at some point in its execution, P4 executes the assignment c = b + c. if P3 executes its assignment statement first, then the final values of b and c are :
b = 3 and c = 5
b = 5 and c = 3
b = 3 and c = 4
b = 4 and c = 3
[ Option A ]
Q: Result obtained from subtracting (1001)2 from (1100)2 is:
(1100)2
(0011)2
(0001)2
(1001)2
[ Option B ]
Binary subtraction works similarly to decimal subtraction, with borrowing done in base 2. When we subtract (1001)2 from (1100)2, we first convert them to decimal to understand the operation, 12 minus 9 equals 3. Converting 3 back to binary gives (0011)2. Therefore, the result obtained from subtracting (1001)2 from (1100)2 is (0011)2.
Q: Consider a system with five processes P0 to P4 and three resource types A, B, C. suppose that, at time T0, the following snapshot of the system has been taken:
| Allocation | Need | Available | |
|---|---|---|---|
| ABC | ABC | ABC | |
| P0 | 010 | 743 | 230 |
| P1 | 302 | 020 | |
| P2 | 302 | 600 | |
| P3 | 211 | 011 | |
| P4 | 002 | 431 |
Check whether a request for (0,2,0) by P0 can be granted according to Banker’s Algorithm?
Yes (Request can be granted)
No (Request cannot be granted)
Cannot be decided
Resulting state is safe
[ Option B ]
Banker’s Algorithm is used in operating systems to avoid deadlock by ensuring that resource allocation keeps the system in a safe state.
Steps to check if a request can be granted:
Q: Which of the following medium access mechanism use in Ethernet?
CSMA/CD
CSMA/CA
Token passing
ALOHA
[ Option A ]
Ethernet is the most widely used Local Area Network (LAN) technology. It defines both the Physical Layer (cabling, signaling) and the Data Link Layer (framing, access control). Because multiple devices share the same communication medium, Ethernet uses a Medium Access Control (MAC) mechanism to decide who can transmit at a given time.
The original Ethernet (Coaxial) and early shared-media Ethernet used CSMA/CD (Carrier Sense Multiple Access with Collision Detection).
| LAN TYPE | MEDIUM ACCESS MECHANISM | COLLISION STATUS |
|---|---|---|
| Ethernet | CSMA/CD | Collision-Prone, detects and retransmits. |
| Wi-Fi (802.11) | CSMA/CA | Collision avoidance, uses RTS/CTS. |
| Token Ring | Token Passing | Collision-free. |
| ALOHA Networks | ALOHA | Collision-prone, retransmit on collision. |
Q: Which of the following is saved during a context switch?
Only the process ID
CPU register values, memory information and process state
Network status and battery level
Only the process priority
[ Option B ]
A context switch occurs when the CPU switches from executing one process (or thread) to another.
During this switch, the state (context) of the currently running process must be saved so that it can resume later exactly where it left off. The new process’s context is then loaded so that it can continue its execution.
The context of a process is stored in a special data structure called the Process Control Block (PCB).
The system saves all the information required to restart the process later, including, CPU Register Values (like program counter, accumulator, etc.), Process State (e.g., ready, waiting, running), Memory Management Information (base and limit registers, page tables, etc.)
This ensures that when the process resumes, it continues execution from the exact same point.
Q: Choose the correct option considering the assertion and reason in context of software engineering.
Assertion (A): The Spiral Model supports progressive refinement of the software product through multiple iterations.
Reason (R): Each pass through the planning region in spiral allows for feedback-based adjustments to cost, schedule, and the number of iterations.
Both (A) and (R) are true, and (R) is the correct explanation of (A).
Both (A) and (R) are true, but (R) is not the correct explanation of (A).
(A) is true, but (R) is false.
(A) is false, but (R) is true.
[ Option A ]
The Spiral Model is an evolutionary software development process model that combines features of both iterative development and the waterfall model. It focuses on risk management and progressive refinement of the software through multiple iterations (spirals).
Each loop (or spiral) of the model consists of four main phases, Planning, Risk Analysis, Engineering, and Evaluation. During each pass through the planning region, teams gather feedback, reassess risks, and adjust cost, schedule, and number of iterations based on real project outcomes.
Q: In usual notations, the expression (p ∧ ~q) → (q ∨ ~p) is logically equivalent to
~q → p
p → ~q
p → q
q → p
[ Option C ]
| p | q | ~q | ~p | p ∧ ~q | q ∨ ~p | (p ∧ ~q) → (q ∨ ~p) | p → q |
|---|---|---|---|---|---|---|---|
| T | T | F | F | F | T | T | T |
| T | F | T | F | T | F ∨ F = F | F | F |
| F | T | F | T | F | T ∨ T = T | T | T |
| F | F | T | T | F | F ∨ T = T | T | T |
Q: The octal equivalent of binary number (1110100.0100111)2 is:
(062.137)8
(264.235)8
(164.234)8
(153.235)8
[ Option C ]
To convert the binary number (1110100.0100111)₂ into octal, we divide the digits into groups of three bits each, starting from the binary point.
For the integer part, grouping (1110100)₂ as (001 110 100) gives octal digits 1, 6, and 4 respectively, forming (164)₈.
For the fractional part, grouping (0100111)₂ as (010 011 100) gives octal digits 2, 3, and 4, forming (.234)₈.
Thus, the octal equivalent of (1110100.0100111)₂ is (164.234)₈.
Q: A/An ___________ is any condition that the database must always satisfy. Domain constraints and referential-integrity constraints are special forms of ___________. Choose the ordered pair to correctly fill in the blanks.
trigger, assertion
assertion, trigger
procedure, function
assertion, assertion
[ Option D ]
In a database, an Assertion is a logical condition that defines a rule or constraint which must always be satisfied by the data in the database. It ensures the consistency and correctness of stored data.
Common examples of assertions include domain constraints, which restrict the permissible values of an attribute, and referential integrity constraints, which ensure valid relationships between tables.
Q: Which of the following SQL operations is used to remove a specific tuple from a relation?
DROP
DELETE
TRUNCATE
REMOVE
[ Option B ]
In SQL, removing data from a table can be done using different commands, but each serves a different purpose. The DROP command deletes the entire table (with all its data and structure), while TRUNCATE removes all rows quickly but keeps the table structure.
To remove a specific tuple or row from a table, the DELETE statement is used with a WHERE clause to target the exact tuple. If no condition is given (in WHERE clause), all rows are deleted but the table structure remains. This ensures that only the intended row is deleted without affecting the rest of the table.
A Database Object is any structure or entity in a database that is created to store, manage, or manipulate data. Examples of database objects include tables, views, indexes, sequences, triggers, procedures, functions, etc.
| Category | Command | Description | Example |
|---|---|---|---|
| DDL (Data Definition Language) | CREATE | Creates a new database, table, or other database object. | CREATE TABLE Students (Rollno INT, Name VARCHAR(50)); |
| ALTER | Modifies the structure of an existing database object (add/drop column, change datatype). | ALTER TABLE Students ADD Age INT; | |
| DROP | Deletes a database, table, or object permanently. | DROP TABLE Students; | |
| TRUNCATE | Deletes all rows from a table but keeps the table structure. | TRUNCATE TABLE Students; | |
| RENAME | Renames a table or database object. | ALTER TABLE Students RENAME TO PGStudent; | |
| DML (Data Manipulation Language) | INSERT | Adds new rows (tuples) to a table. | INSERT INTO Students VALUES (1001, 'Suresh'); |
| UPDATE | Modifies existing rows in a table. | UPDATE Students SET Age = 31 WHERE Rollno = 1001; | |
| DELETE | Removes specific rows from a table. | DELETE FROM Students WHERE Rollno= 1001; | |
| DCL (Data Control Language) | GRANT | Gives privileges/permissions to users. | GRANT SELECT, INSERT ON Students TO User1; |
| REVOKE | Removes privileges/permissions from users. | REVOKE INSERT ON Students FROM User1; | |
| DQL (Data Query Language) | SELECT | Retrieves data from one or more tables. | SELECT Name, Age FROM Students; |
| TCL (Transaction Control Language) | COMMIT | Saves all changes made in the current transaction permanently. | COMMIT; |
| ROLLBACK | Undoes all changes made in the current transaction. | ROLLBACK; | |
| SAVEPOINT | Sets a point within a transaction to which you can roll back. | SAVEPOINT sp1; |
Q: What is a delivery approach to software development where some of the developed increments are delivered to the customer and deployed for use in an operational environment?
Forward delivery
Incremental delivery
Backward delivery
Decremental delivery
[ Option B ]
In software development, the Incremental Delivery Approach is a method where the system is designed, implemented, and delivered in small, manageable increments rather than all at once. Each increment represents a part of the overall functionality and can be deployed to the customer for use in a real operational environment. This approach allows:
Q: Which cloud computing model delivers applications over the internet, allowing users to access services like word processing and CRM without installing them locally?
Infrastructure as a Service (IaaS)
Software as a Service (SaaS)
Platform as a Service (PaaS)
Hardware as a Service (HaaS)
[ Option B ]
In cloud computing, different service models provide varying levels of resources and management. Software as a Service (SaaS) is the model that delivers applications over the internet, allowing users to access software such as word processors, Customer Relationship Management (CRM) tools, or email clients without installing them locally.
| CLOUD SERVICE MODEL | DESCRIPTION |
|---|---|
| Infrastructure as a Service (IaaS) | Provides virtualized computing resources over the internet, including servers, storage, and networking. Users manage OS, applications, and data while the provider manages hardware. |
| Platform as a Service (PaaS) | Provides a platform for developers to build, test, and deploy applications without worrying about underlying infrastructure. Includes OS, middleware, and runtime environment. |
| Software as a Service (SaaS) | Delivers software applications over the internet. Users access applications via web browsers or thin clients without installing locally. Provider manages everything from infrastructure to software updates. |
Q: A receiver using Manchester decoding expects a transition in every bit period. If the line goes from high to high during one bit period, what does the receiver most likely interpret?
Bit 0
Bit 1
Bit error or synchronization loss
Bit 1 followed by Bit 0
[ Option C ]
In Manchester Encoding, each bit period must have a transition in the middle, Low to High for bit 1 and High to Low for bit 0. This transition helps maintain synchronization between sender and receiver. If the line stays high throughout a bit period (High to High), it means no transition occurred, violating the Manchester rule. Therefore, the receiver interprets it as a bit error or loss of synchronization.
Q: How many unique states can a K-bit switch tail ring counter generate?
2K
Kn
2K
K
[ Option A ]
Q: A plain text message may be hidden in one of two ways. The methods of _________ conceal the existence of the message, whereas the methods of __________ render the message unintelligible to outsiders by various transformations of the text.
Choose the valid ordered pair to fill in the blanks.
steganography, cryptography
cryptography, steganography
encoding, decoding
authentication, hashing
[ Option A ]
A plain text message can be hidden or protected in two main ways. Steganography is the technique used to conceal the existence of the message itself. For example, a secret message might be hidden inside an image or audio file in such a way that outsiders cannot even detect that a message exists.
Cryptography transforms plaintext into ciphertext via encryption, rendering the content unintelligible to outsiders without the decryption key.
Q: In the context of SQL standard, which of the following statement(s) is/are true?
I: Table function can be used in a Query.
II: Procedures are invoked by using a call statement.
only I
only II
Both I and II
Neither I nor II
[ Option C ]
A table function is a user-defined function that returns a table and can be used within a query’s FROM clause, allowing it to behave like a regular table.
Similarly, stored procedures are invoked using the CALL statement, which is the standard method for executing procedures in SQL. Therefore, both statements I and II are correct.
Q:
Match the OSI layers in Column – I with their tasks in Column – II:
| Column – I | Column – II |
|---|---|
| a. Data Link Layer | i. End-to-end communication between source and destination programs. |
| b. Transport Layer | ii. The sender breaks up the input data into data frames and transmits the frames sequentially. |
| c. Network Layer | iii. Routing and forwarding. |
| iv. Concerned with the syntax and semantics of the information transmitted. |
a-ii, b-i, c-iii
a-iv, b-ii, c-i
a-iii, b-i, c-iv
a-i, b-iii, c-ii
[ Option A ]
| OSI LAYER | DATA UNIT | DESCRIPTION | DELIVERY |
|---|---|---|---|
| Physical | Bits | Transmits raw binary data over physical medium and defines cables, connectors, voltages, and signals. | Node to Node |
| Data Link | Frame | Provides error detection and correction and reliable transfer between adjacent nodes and handles MAC addressing. Framing. | Node (Hop) to Node (Hop) |
| Network | Packet | Determines the best path for data transmission and handles logical addressing (IP Addresses), routing and forwarding. | Host to Host |
| Transport | Segment | Ensures reliable data transfer, flow control and error recovery, TCP and UDP operate here. | Process to Process / End-to-End |
| Session | Data | Manages sessions and connections between applications, establishes, maintains, and terminates sessions. | Process to Process / End-to-End |
| Presentation | Data | Translates, encrypts, compresses, or formats data for the application and ensures data is in usable form. | Process to Process / End-to-End |
| Application | Data | Provides network services to end-user applications like email, file transfer, and web browsing. | End-to-End |
Q: How many address lines are needed to address a memory of 512 bytes?
6
7
8
9
[ Option D ]
Address Lines in Memory
Given: Memory size = 512 bytes
Number of address lines n is calculated using:
2n = Memory size in bytes
2n = 512
Since 29=512, we find n=9.
Q: Which of the following algorithms uses the greedy approach to find a Minimum Spanning Tree (MST)?
Bellman-Ford Algorithm
Kruskal’s and Prim’s Algorithm
Floyd-Warshall Algorithm
Dijkstra’s Algorithm
[ Option B ]
A Minimum Spanning Tree (MST) is a subset of the edges of a connected, weighted graph that:
Algorithms for MST:
Bonus:
Q: What is true about the height h of a B-tree with n keys (n ≥ 1) and minimum degree t ≥ 2 ?
h ≤ logt(n) + 1
h ≤ logt((n + 1) / 2)
h ≤ logt(n-1)
h ≤ log2(n)
[ Option B ]
Q: What is the time complexity of inserting an element at the beginning of a linked list?
O(n)
O(log n)
O (n log n)
O(1)
[ Option D ]
In a linked list, each node contains data (info) and a pointer to the next node (link). When inserting a new element at the beginning of the list, we simply create a new node, set its link to point to the current first node, and then update the head (start) pointer to this new node.
These operations take a constant amount of time because there is no need to traverse the list or move any existing elements. Therefore, the time complexity of inserting an element at the beginning of a linked list is O(1), which means it executes in constant time regardless of the size of the list.
Q: In a multithreaded process, which of the following is not shared among threads?
Registers
Data
Code
Files
[ Option A ]
In a Multithreaded Process, multiple threads run within the same process and share certain resources to efficiently perform tasks concurrently. Threads belonging to the same process share the code section, data section, and files.
However, each thread requires its own Registers and Stack to keep track of its current state, local variables, and execution context.
Q: Consider a logical address 0001001011110000, which representing segment number 1 (leftmost 4 bits) and offset 752. Suppose that this segment is residing in main memory starting at physical address 0010000000100000, then, the physical address of the segment is :
0010001100010000
0010001000011000
0001000101010000
0010000011011000
[ Option A ]
Q: Consider Column – I and Column – II in context of software testing.
| Column – I | Column – II |
|---|---|
| a. Basis Path Testing | i. Recovery Testing |
| b. Smoke Testing | ii. Alpha and Beta Testing |
| c. System Testing | iii. While Box Testing |
| d. Acceptance Testing | iv. Integration Testing |
Which of the following is the most suitable Match of Column – I and Column – II?
a-iv, b-i, c-iii, d-ii
a-iii, b-ii, c-iv, d-i
a-iii, b-iv, c-i, d-ii
a-ii, b-iv, c-i, d-iii
[ Option C ]
| TESTING TYPE | EXPLANATION |
|---|---|
| Basis Path Testing | Basis Path Testing is a white-box testing technique that focuses on the internal logic and structure of the code. It uses control flow graphs to identify all possible execution paths. |
| Smoke Testing | Smoke Testing is a preliminary integration test performed after building a software module to ensure that the major functionalities work and the build is stable for further testing. |
| System Testing | System Testing includes different types of testing such as recovery testing, which checks how well a system can recover from crashes, failures, or hardware issues. |
| Acceptance Testing | Acceptance Testing verifies whether the system meets business requirements. It includes Alpha and Beta Testing, which are conducted by end users before final deployment. |
| TESTING TYPE | EXPLANATION |
|---|---|
| Unit Testing | Tests individual components or functions of the program to ensure each part works correctly in isolation. Usually performed by developers. |
| Integration Testing | Checks the interaction between integrated modules or units to identify interface-related defects. |
| System Testing | Tests the complete integrated system as a whole to verify that it meets the specified requirements. |
| Acceptance Testing | Conducted to ensure the software is ready for delivery. It validates whether the system meets business needs. Includes Alpha and Beta testing. |
| Alpha Testing | Performed by internal users or testers at the developer’s site to identify defects before releasing to customers. |
| Beta Testing | Conducted by selected end-users in a real-world environment to gather feedback before the final release. |
| Smoke Testing | A quick test after a new build to ensure that major functionalities are working and the build is stable for further testing. |
| Sanity Testing | Conducted after receiving a software build to check specific functionality or bug fixes. It ensures that the changes did not break existing features. |
| Regression Testing | Performed to confirm that recent code changes have not affected the existing functionalities. |
| Performance Testing | Evaluates the system’s speed, stability, and responsiveness under different workloads. |
| Load Testing | Tests how the system behaves under expected user loads to identify performance bottlenecks. |
| Stress Testing | Determines the system’s breaking point by testing it under extreme conditions or heavy load. |
| Recovery Testing | Verifies how well the system recovers from crashes, power failures, or network outages. |
| Usability Testing | Assesses how user-friendly, efficient, and easy to navigate the software is for end-users. |
| Compatibility Testing | Checks whether the software works properly on different devices, operating systems, and browsers. |
| White Box Testing | Examines the internal code structure and logic of the software. Used mainly by developers. |
| Black Box Testing | Focuses on external behavior of the software without looking at the internal code. Used mainly by testers. |
| Gray Box Testing | Combines aspects of both white-box and black-box testing. Testers have partial knowledge of internal design. |
| Mutation Testing | Introduces small changes (mutations) in the code to check if existing test cases can detect them, ensuring test quality. |
| Ad-hoc Testing | Performed without any formal plan or test cases, relying on tester’s intuition and experience. |
Q: Which of the following is not true about a complete graph with n vertices?
Each vertex has degree n-1
It contains no cycle
It is connected
It has n(n-1)/2 edges
[ Option B ]
In graph theory, a Complete Graph is a simple graph in which every pair of distinct vertices is connected by an edge.
Q: A linked list (without header node) contains 3 nodes. The nodes are self-referential structures having a node pointer (name Link) apart from the information. Let START is pointer to the first node and END is pointer to the last node of the linked list. If the following C statements are executed in order, what will happen?
(X is a pointer of node type)
X=START->Link;
START->Link = X->Link;
free(X);
First Node will be deleted
Last Node will be deleted
START pointer will become NULL
Middle Node will be deleted
[ Option D ]
In this,
Q: What is the primary difference between a schema and an instance in a database?
Schema changes frequently while instance remains constant.
Schema is data at a moment, instance is its structure.
Schema is the structure, instance is the data.
Schema and instance are always identical.
[ Option C ]
The Schema refers to the overall design or structure of the database, defining how data is organized, such as the tables, fields, and relationships among them. It acts as a blueprint and usually remains unchanged over time.
An Instance represents the actual data stored in the database at a particular point in time. Since data is constantly being inserted, updated, or deleted, instances change frequently.
Therefore, the primary difference is that the schema defines the structure, while the instance represents the data.
Q: Which of the following is TRUE about a hypervisor in a virtualized system?
It lets each guest OS control hardware and manage other VMs.
It allows secure sharing of hardware among multiple guest OSs.
It enables guest OSs to run in kernel mode and manage devices.
It isolates VMs but prevents live migration between platforms.
[ Option B ]
A Hypervisor is a software layer that enables virtualization, allowing multiple guest operating systems (OSs) to run simultaneously on a single physical machine. It manages and allocates hardware resources securely among the virtual machines (VMs), ensuring that each VM operates independently without interfering with others.
Hypervisors do not allow guest OSs to directly control hardware or run in kernel mode for managing devices.
Q: We want to digitize a human voice signal. Assuming that each audio sample is represented using 8 bits and the human voice normally contains frequencies from 0 to 4000 Hz. What is the resulting bit rate of the digitized signal?
128 kbps
32 kbps
64 kbps
256 kbps
[ Option C ]
To digitize a human voice signal, the Pulse Code Modulation (PCM) method is used, which requires sampling the analog signal.
According to the Nyquist theorem, the sampling rate must be at least twice the highest frequency present in the signal.
Since the human voice ranges up to 4000 Hz, the signal must be sampled at 8000 samples per second. If each sample is represented by 8 bits, the total bit rate becomes 8000 × 8 = 64,000 bits per second, or 64 kbps.
Q: Which of the following is/are true statement(s) in C++?
S1 : Function can be overloaded
S2 : Operator can be overloaded
S3 : Constructor can be overloaded
S1 and S2 only
S1, S2 and S3
S2 only
S3 and S2 only
[ Option B ]
In C++, Overloading allows multiple functions, operators, or constructors to have the same name but behave differently based on their parameters (either number, type or sequence of parameters).
S1: Function can be overloaded – True. We can have multiple functions with the same name but different number or types or sequence of parameters.
S2: Operator can be overloaded – True. Operator overloading allows defining custom behaviors for operators (like +, -, *, == etc.) for user-defined types (classes). This means you can change how operators work with your objects.
class Complex {
int real, imag;
public:
Complex operator+(Complex const &c) {
Complex temp;
temp.real = real + c.real;
temp.imag = imag + c.imag;
return(temp);
}
};
S3: Constructor can be overloaded – True. Constructors are special functions called when objects are created. A class can have multiple constructors with different parameter lists.
class MyClass {
public:
MyClass() {} // default constructor
MyClass(int a) {} // one argument constructor
MyClass(int a, int b) {} // two argument constructor
};
Q: A die is thrown two times. Sum of the obtained numbers is multiple of 4. The probability, that digit 4 has appeared at least once, is
2/9
4/9
1/8
1/9
[ Option D ]
Q:
Match the following modes of communications in Column – I to their descriptions in Column – II:
| Column – I | Column – II |
|---|---|
| a. Simplex | i. Links that allow traffic in only one direction. |
| b. Half-Duplex | ii. Links that can be used in both directions at the same time. |
| c. Full-Duplex | iii. Links that can be used in either direction, but only one way at a time. |
a – i, b – iii, c – ii
a – ii, b – iii, c – i
a – iii, b – ii, c – i
a – ii, b – i, c – iii
[ Option A ]
Modes of data exchange, also called communication modes, describe how data flows between two devices.
| TRANSMISSION MODE | DESCRIPTION | EXAMPLE |
|---|---|---|
| Simplex | Data flows in only one direction, one device is sender, the other is receiver. | TV broadcast, Keyboard to computer input. |
| Half-Duplex | Data can flow in both directions, but only one direction at a time. | Walkie-Talkie. |
| Full-Duplex | Data flows in both directions simultaneously. | Telephone conversation. |
Q: Which of the following is a collision-free access control mechanism?
ALOHA
CSMA/CA
Token Passing
CSMA/CD
[ Option C ]
In computer networks, multiple devices share a common communication medium. To avoid conflicts when two devices try to transmit simultaneously, access control mechanisms are used. These mechanisms can be Collision-Prone or Collision-Free:
Q: Match the correct description :
| Column – I | Column – II |
|---|---|
| a. Throughput | i. Time from process submission to its first response being produced. |
| b. Turnaround Time | ii. Number of processes completed per unit of time. |
| c. Waiting Time | iii. Total time a process spends in the ready queue waiting for the CPU. |
| d. Response Time | iv. Total time from process submission to its completion, doing I/O, waiting in the ready queue, and executing on the CPU. |
Choose the correct option:
a – iv, b – ii, c – iii, d – i
a – ii, b – iii, c – iv, d – i
a – ii, b – iv, c – i, d – iii
a – ii, b – iv, c – iii, d – i
[ Option D ]
In an operating system, CPU scheduling determines the order in which processes are executed. To evaluate scheduling algorithms, we use certain key performance metrics, Throughput, Turnaround Time, Waiting Time, and Response Time.
| METRIC | DEFINITION | FORMULA |
|---|---|---|
| Throughput | Number of processes completed per unit of time. It shows how efficiently the system is processing tasks. | Throughput = (Number of Processes Completed) / (Total Time Taken) |
| Turnaround Time (TAT) | Total time taken from process submission to its completion. | TAT = Completion Time – Arrival Time |
| Waiting Time (WT) | Total time a process spends waiting in the ready queue before execution. | WT = Turnaround Time – Burst Time |
| Response Time (RT) | Time from process submission to the first response (first CPU allocation). | RT = First Response Time – Arrival Time |
| Turnaround Time (Average) | Average of turnaround times of all processes. | Average TAT = Σ(TAT) / Number of Processes |
| Waiting Time (Average) | Average of waiting times of all processes. | Average WT = Σ(WT) / Number of Processes |
Q: In context of ER diagram, the relationship set connecting the weak entity set to the identifying strong entity set is depicted by a ___________ and double lines are used to connect weak entity set to the relationship to indicate ___________ of weak entity set.
double diamond, total participation
dashed diamond, primary key
dashed rectangle, cardinality ratio
double rectangle, discriminator
[ Option A ]
In an ER diagram, a Weak Entity Set cannot be uniquely identified by its own attributes and relies on a Strong (Identifying) Entity Set for uniqueness. The relationship that connects a weak entity to its identifying strong entity is known as the identifying relationship. This relationship is depicted using a Double Diamond symbol.
Since every weak entity must be associated with a strong entity, there is Total Participation, which is represented by Double Lines connecting the weak entity set to the identifying relationship.
Q: Which of the following is not a transport layer protocol in TCP/IP protocol suite?
TCP
SNMP
SCTP
UDP
[ Option B ]
In the TCP/IP Protocol Suite, the Transport Layer (OSI Model Layer 4) is responsible for providing end-to-end communication services for applications. Its main functions include reliable data delivery, flow control, error detection, and multiplexing.
TCP, UDP, and SCTP are transport layer protocols in the TCP/IP suite. TCP is reliable and connection-oriented, UDP is connectionless, SCTP is a message-oriented, reliable transport with multi-homing and multi-streaming.
SNMP (Simple Network Management Protocol) is an application layer protocol used for network management.
| LAYER NAME | COMMONLY USED PROTOCOLS |
|---|---|
| Application | HTTP, HTTPS, FTP, SFTP, SMTP, IMAP, POP3, DNS, DHCP, SNMP, Telnet, SSH, NTP |
| Presentation | TLS/SSL, MIME, JPEG, PNG, GIF, MPEG, ASCII/EBCDIC Conversion |
| Session | RPC, NetBIOS Sessions, PPTP, SMB |
| Transport | TCP, UDP, SCTP, DCCP, QUIC |
| Network | IP (IPv4/IPv6), ICMP, IGMP, ARP/ND, OSPF, RIP, BGP, IS-IS |
| Data Link | Ethernet (IEEE 802.3 MAC), Wi Fi 802.11 MAC, PPP, HDLC, Frame Relay, ATM, MPLS, ARP |
| Physical | Ethernet (IEEE 802.3), Wi Fi (802.11), SONET/SDH, DSL, Fiber, Coax, Bluetooth PHY, USB, ISDN |
Q: Which of the following is not a part of IPv4 datagram header?
Time to live
Fragmentation Offset
Source IP address
Recursion field
[ Option D ]
An IPv4 datagram header contains crucial information that helps routers deliver packets from the source to the destination across networks. Each field in the header has a specific role, such as identifying the packet, handling fragmentation, or limiting its lifetime in the network.
The IPv4 header is typically 20 bytes minimum it can grow up to 60 bytes. It contains fields like version, header length, type of service, total length, identification, flags, fragmentation offset, time to live (TTL), protocol, header checksum, source IP, and destination IP.
| FIELD NAME | SIZE |
|---|---|
| Version | 4 bits |
| IHL (Internet Header Length) | 4 bits |
| DSCP (Differentiated Services Code Point) | 6 bits |
| ECN (Explicit Congestion Notification) | 2 bits |
| Total Length | 16 bits |
| Identification | 16 bits |
| Flags | 3 bits |
| Fragment Offset | 13 bits |
| Time To Live (TTL) | 8 bits |
| Protocol | 8 bits |
| Header Checksum | 16 bits |
| Source IP Address | 32 bits |
| Destination IP Address | 32 bits |
| Options (if present) | Variable Length |
| Padding (if options present) | Variable Length |
IHL stands for Internet Header Length. It is a 4-bit field in the IPv4 header that specifies the length of the IPv4 header in 32-bit words.
The minimum value is 5 (5 × 32 bits = 20 bytes, when there are no options) and the maximum is 15 (15 × 32 bits = 60 bytes, when options are present). To get the header size in bytes, multiply the IHL value by 4.
Q: In public key cryptography, which key is used to verify a digital signature?
Sender’s private key
Sender’s public key
Receiver’s public key
Receiver’s private key
[ Option B ]
In public key cryptography, a Digital Signature is created by the sender using their private key. To verify that the signature is authentic and that the message has not been altered, the receiver uses the sender’s public key. This ensures the signature was indeed generated by the sender and provides authentication and integrity.
Q:
Consider the five processes with given arrival and service times. What will be the average turnaround time for Shortest Process Next (SPN) scheduling algorithm?
| Process | Arrival Time | Service Time (Ts) |
|---|---|---|
| A | 0 | 3 |
| B | 2 | 6 |
| C | 4 | 4 |
| D | 6 | 5 |
| E | 8 | 2 |
7.6
7.2
7.8
8
[ Option A ]
SPN (Shortest Process Next), also known as Shortest Job First (SJF) (non-preemptive), is a CPU scheduling algorithm that selects the ready process with the shortest service (burst) time for execution next. The goal is to minimize the average waiting and turnaround times.
Turnaround Time (TAT) = Completion Time − Arrival Time.
| PROCESS | ARRIVAL | COMPLETION | TURNAROUND TIME |
|---|---|---|---|
| A | 0 | 3 | 3 – 0 = 3 |
| B | 2 | 9 | 9 – 2 = 7 |
| E | 8 | 11 | 11 – 8 = 3 |
| C | 4 | 15 | 15 – 4 = 11 |
| D | 6 | 20 | 20 – 6 = 14 |
Total Turnaround Time = 3 + 7 + 3 + 11 + 14 = 38
Average Turnaround Time = 38 / 5 = 7.6
Q: How many decade counters are connected in cascade to count from 0 to 999?
5
6
9
3
[ Option D ]
Q: Consider the relation course(courseld, cname, credits, deptNo) and two queries Q1 and Q2.
Q1: select deptNo, sum(credits) as totalCredits1 from course group by deptNo having totalCredits1 = ANY (select max(x.totalCredits) from (select sum(credits) as totalCredits from course group by deptNo) as x);
Q2: select deptNo, sum(credits) as totalCredits1 from course group by deptNo having totalCredits1 >= ALL (select sum(credits) from course group by deptNo);
Q1 will give same result as Q2.
Q2 result will be subset of Q1 result.
Q1 result will be subset of Q2 result.
Q1 and Q2 will give different results.
[ Option A ]
Both queries aim to find the department(s) with the maximum total credits from the course relation.
Query Q1 uses a nested subquery with ANY and MAX to select the department(s) whose total credits equal the maximum total credits.
Query Q2 uses >= ALL on a subquery that computes the total credits per department, which also selects department(s) having the highest total credits.
Q: Which of the following is not provided by Digital Signature directly?
Authentication
Integrity
Non-repudiation
Confidential communication
[ Option D ]
A Digital Signature is a cryptographic tool used to verify the authenticity and integrity of a message. It ensures that the sender of the message can be verified (Authentication) and that the message has not been altered in transit (Integrity). Digital signatures also provide Non-Repudiation, meaning the sender cannot deny having sent the message.
| Feature | Explanation |
|---|---|
| Authentication | Verifies the identity of the sender. |
| Integrity | Ensures the message has not been altered. |
| Non-repudiation | Prevents the sender from denying they sent the message. |
However, Digital Signatures do not provide Confidentiality, they do not encrypt the content of the message.
Q: A computer with cache access time of 100 ns, a main memory access time of 1000 ns, and a hit ratio of 0.9 produces an average memory access time of
1100 ns
200 ns
900 ns
150 ns
[ Option B ]
Cache memory is a small, high-speed memory placed between the CPU and main memory to reduce access time. Average Memory Access Time (AMAT) is calculated using the formula:
AMAT = (Hit Ratio × Cache Access Time) + (Miss Ratio × Main Memory Access Time)
Given:
Cache access time = 100 ns
Main memory access time = 1000 ns
Hit ratio = 0.9
Miss Ratio=1−0.9=0.1
AMAT = (0.9×100) + (0.1×1000) = 90 + 100 = 190 ns
Approximating to the closest option gives 200 ns.
Q: The converse, contrapositive and inverse statements of p → q are respectively –
p → ~q, q → p, ~p → q
q → p, ~q → ~p, ~p → q
q → p, ~p → ~q, ~p → q
q → p, ~q → ~p, ~q → ~p
[ Option B ]
| Statement Type | Expression |
|---|---|
| Converse | q → p |
| Contrapositive | ~q → ~p |
| Inverse | ~p → ~q |
Q: (FE35)16 XOR (CB15)16 is equal to
(FF35)16
(FF50)16
(3520)16
(3320)16
[ Option C ]
To perform XOR between two hexadecimal numbers, each hex digit is first converted into its 4-bit binary equivalent. For (FE35)₁₆ and (CB15)₁₆, the binary forms are 1111111000110101 and 1100101100010101, respectively. Performing bitwise XOR gives 0011 0101 0010 0000, which in hexadecimal is (3520)₁₆.
(FE35)16 ⊕ (CB15)16
First of all, write both numbers in binary form, so,
| Hexadecimal | Binary (4 bits) |
|---|---|
| F | 1111 |
| E | 1110 |
| 3 | 0011 |
| 5 | 0101 |
| C | 1100 |
| B | 1011 |
| 1 | 0001 |
| 5 | 0101 |
So,
FE35 = 1111 1110 0011 0101
CB15 = 1100 1011 0001 0101
Perform bitwise XOR:
| Pair | XOR result | Hexadecimal |
|---|---|---|
| F (1111) ⊕ C (1100) | 0011 | 3 |
| E (1110) ⊕ B (1011) | 0101 | 5 |
| 3 (0011) ⊕ 1 (0001) | 0010 | 2 |
| 5 (0101) ⊕ 5 (0101) | 0000 | 0 |
Finally, (FE35)16⊕(CB15)16 = (3520)16.
Q: In data transfer by peripheral devices, which of the following statement is correct?
CPU is kept in loop to check whether data is available.
CPU assumes that a peripheral is always available.
SOD pin is used.
When a peripheral is ready, it sends interrupt signal to the CPU to transfer data.
[ Option D ]
Data Transfer by Peripheral Devices
Q: A condition in which a process is spending more time paging than executing is called:
Race condition
Thrashing
Aging
Virtualization
[ Option B ]
Thrashing occurs in a paging system when a process spends more time swapping pages in and out of memory than executing instructions.
It typically happens when the system does not have enough physical memory to hold the working set of all active processes. Thrashing leads to severe performance degradation, as the CPU is mostly idle waiting for page transfers.
Q: If A = {x ∈ R : |x + 1| < 2} and B = {x ∈ R : |x − 1| ≥ 2}, then (B – A) is equal to (where R is set of real numbers)
R – (–1, 1)
R – (–3, 3)
(–1, 1)
(–3, 3)
[ Option B ]
Q: Which of the following statements about virtual methods in C++ is TRUE?
Constructors in C++ can be declared as virtual to support polymorphism.
Redefining a virtual method in a derived class requires the same signature and return type as in the base class.
A function in a base class becomes virtual if it is declared virtual in any of its derived classes.
A virtual method must be redefined in every derived class, otherwise it leads to a compilation error.
[ Option B ]
Q: In Object-Relational Data Models, which of the following is true about attributes of tuples?
Only scalar atomic value attributes are allowed.
Only string value attributes are allowed.
Attributes of complex types including nested relation are allowed.
Only Boolean value attributes are allowed.
[ Option C ]
In Object-Relational Data Models (ORDM), the traditional relational restriction that each attribute must be atomic is relaxed. Tuples can have attributes of complex types, such as nested relations, arrays, or objects. This allows the database to better model real-world entities and relationships while retaining relational principles.
Q: Which of the following control measures is not corresponding to database security?
Access control
Interface control
Flow control
Data encryption
[ Option B ]
Database Security refers to protecting data from unauthorized access, misuse, or corruption. To ensure data integrity and privacy, several control measures are implemented within a database system.
| SECURITY MECHANISM | DESCRIPTION |
|---|---|
| Access Control | Restricts user access to database objects based on permissions. Ensures only authorized users can read, insert, update, or delete data. |
| Authentication | Verifies user identity before allowing access, can use passwords, biometrics, or multi-factor authentication. |
| Authorization | Defines user roles and privileges after authentication, ensures users perform only allowed operations. |
| Encryption | Protects data confidentiality by converting it into unreadable format, applies to data at rest and data in transit. |
| Audit Trails / Logging | Records user activities and database operations. Helps detect misuse and ensures accountability. |
| Flow Control | Prevents data from flowing between unauthorized levels or entities. Ensures multilevel security. |
| Backup and Recovery | Maintains copies of data to restore in case of failure or loss. Protects data integrity and availability. |
| Physical Security | Protects hardware and storage from unauthorized access or damage. Ensures overall system security. |
Q: Which of the following is not a type of firewall?
Stateful Inspection
Application Proxy
Packet Filtering
ITU-T X.509
[ Option D ]
A Firewall is a network security device or software that monitors and controls incoming and outgoing traffic based on predefined security rules. Common types of firewalls include:
ITU-T X.509 is a standard for Public Key Infrastructure (PKI) certificates and certificate formats used for authentication and trust, not for traffic filtering.
Q: If a branch instruction causes a change in control flow during pipelining,
execution is delayed.
the pipeline is emptied and subsequent instructions are discarded.
only decoding is paused.
no change occurs.
[ Option B ]
Pipelining is a technique in CPUs where multiple instructions are overlapped in execution to improve performance. A branch instruction changes the normal sequential flow of execution by jumping to a different memory address. This can cause a control hazard, because the CPU may have already fetched instructions following the branch, which may no longer be correct.
Q: Secondary storage devices are used to store
Small volatile data
Unused data in small quantity
Mass non-volatile data and program
Data for high speed communication like in cache
[ Option C ]
Secondary Storage devices are used for long-term data storage and are non-volatile, meaning the data is retained even when the power is turned off. They provide large storage capacity compared to primary memory (RAM). Examples include Hard Disks Drive (HDD), SSDs, CDs, and DVDs.
These devices are not used for high-speed operations like cache or for small temporary data; instead, they store mass data and programs that are not currently in active use.
Q: Which of the following are four solid dimensions of software feasibility?
Finance, Coding, Time, Security
Finance, Technology, Time, Resources
Cost, Programmer, Internet, Computer
Hardware, Software, Network, Security
[ Option B ]
In software engineering, Feasibility Study is an essential step in the Software Development Life Cycle (SDLC) that helps determine whether a project is practically achievable before full-scale development begins. The four solid dimensions of software feasibility are:
Q: Consider the schedule S:
Which of the following statements is correct regarding S?
S : w1(A); w1(B); w2(A); r2(B); c2; c1;
Serializable but not recoverable
Both Serializable and Recoverable
Recoverable but not Serializable
Neither Serializable nor Recoverable
[ Option A ]
The schedule S: w1(A); w1(B); w2(A); r2(B); c2; c1; involves two transactions T1 and T2. Checking for Recoverability, T2 reads data written by T1 and commits before T1 commits, which violates recoverable schedule rules. Hence, the schedule is Not Recoverable.
For Serializability, analyzing conflicting operations shows that T1’s writes on A and B conflict with T2’s operations, resulting in a precedence graph with a single edge from T1 to T2. Since the graph is acyclic, the schedule is conflict serializable. Therefore, the schedule is serializable but not recoverable.
Q: Which of the following is a valid value that can be stored in a variable of type NUMERIC(4, 1) in SQL?
444.5
44.55
4.555
3333.5
[ Option A ]
In SQL, a column defined as NUMERIC(4, 1) can store a total of four digits, out of which one digit is reserved for the decimal part and the remaining three for the integer part. Hence, valid numbers range approximately from –999.9 to 999.9. Among the given options, only 444.5 satisfies these conditions.
So, in SQL,
So, for NUMERIC(4, 1):
Q: Five-digit numbers are formed using digits from the set {1, 2, 3, 4, 5} and the repetition of digits is allowed. If these numbers are divisible by 4, then total number of such numbers is
25
125
625
3125
[ Option C ]
To form a five-digit number divisible by 4 using digits {1,2,3,4,5} with repetition allowed, we first check the last two digits because a number is divisible by 4 if its last two digits form a number divisible by 4. The valid last-two-digit combinations are 12, 24, 32, 44, and 52, giving 5 options. The first three digits can be any of the 5 digits, so there are 5×5×5=125 ways. Multiplying the options for the first three digits and the last two digits gives 125×5=625. Hence, there are 625 such numbers.
Q: Consider the following statements:
A: Multithreaded applications are characterized by having a small number of highly threaded processes.
B: Multiprocess applications are characterized by the presence of many single-threaded processes.
Which of the following is true about the above statements?
Only A is correct.
Only B is correct.
Neither A nor B is correct.
Both A and B are correct.
[ Option D ]
Multithreading refers to a programming model where multiple threads run within the same process, sharing the same memory space but executing different tasks concurrently.
Multiprocessing, on the other hand, uses multiple processes, each with its own separate memory and resources.
Q: The numbers of selection lines for 8 to 1 multiplexer are :
4
1
3
2
[ Option C ]
For a multiplexer, the number of select inputs is decided by the relation,
Select Inputs=log2(Number of Data Inputs)
An 8:1 multiplexer has 8 data inputs and only one output, which means we need enough select lines to uniquely choose one of the 8 inputs. Since log2(8) = 3, three select inputs are required.
Q: Which condition causes a stack underflow?
Removing from an empty stack
Reading beyond the top
Allocating too much memory
Inserting into a full stack
[ Option A ]
A stack is a linear data structure that follows the LIFO (Last In, First Out) principle. In stack the last element inserted is the first one to be removed. Stack Underflow occurs when an attempt is made to pop (remove) an item from an empty stack, where no elements exist to remove.
Q: For a noiseless channel, the ___________ formula defines the theoretical maximum bit rate.
Nyquist bit rate
Shannon bit rate
Ethernet bit rate
None bit rate
[ Option A ]
For a Noiseless communication channel, the theoretical maximum bit rate is determined by the Nyquist bit rate formula. The Nyquist formula calculates the highest possible data rate based on the channel bandwidth (B) and the number of discrete signal levels (M) used in transmission.
Maximum bit rate = 2 × B × log2(M)
In contrast, the Shannon bit rate formula considers noisy channels and accounts for signal-to-noise ratio (SNR), making it applicable when noise is present.
Q: Which of the following cannot be declared static in C++?
Class
Member variables
Constructor
Function
[ Option C ]
In C++, static can be used in various contexts, but there are restrictions:
(1) You can declare static members inside a class, but not the class itself as static in global scope. However, nested classes inside a class can be declared static. So, this is a bit tricky, but not the correct answer for “cannot be declared static.”
(2) The member variables can be declared static. They belong to the class, not to individual objects.
(3) The functions can be declared as static, either inside a class (meaning it is a class-level function) or in global scope.
(4) The constructor cannot be declared as static in C++, because a constructor is meant to create an instance of a class. But a static function does not have access to this pointer, i.e., it is not tied to any instance. Hence, declaring a constructor as static makes no sense, and is not allowed.
Q: Which statement(s) is/are correct from the following?
S1: If multiple transactions are allowed to execute concurrently, then shadow-paging technique is not applicable.
S2: Log-based techniques can be used, if multiple transactions are allowed to execute concurrently.
S1 only
S2 only
Both S1 and S2
Neither S1 nor S2
[ Option C ]
Shadow Paging keeps a copy of the old page table and replaces it at commit, which makes it incompatible with multiple concurrent transactions because changes cannot be merged safely.
On the other hand, Log-Based Techniques maintain a log of all changes and can safely support multiple concurrent transactions, providing both undo and redo capabilities during recovery.
Q: In Register direct addressing mode, data are accessed by,
specifying the register name in which they are stored.
specifying the memory location in which they are stored.
secondary storage.
specifying the data directly.
[ Option A ]
Register Direct Addressing Mode
So, in Register Direct Addressing Mode, data are accessed by specifying the register name in which they are stored.
Q: In a survey of 100 persons, it was found that 28 read mathematics, 30 read physics, 42 read chemistry, 8 read mathematics and physics, 10 read mathematics and chemistry, 5 read physics and chemistry and 3 read all the three subjects. How many read chemistry only?
27
30
24
33
[ Option B ]
To find the number of students who read chemistry only, we can use a Venn diagram approach. Let M, P, and C represent students reading mathematics, physics, and chemistry, respectively.
Total Chemistry = 42
M ∩ C only = 10 - 3 = 7
P ∩ C only = 5 - 3 = 2
All three = 3
So Chemistry only = 42 - (M ∩ C only + P ∩ C only + all three)
=42 − ( 7 + 2 + 3 ) = 42 – 12 = 30
Q:
Given a 5-bit sequence number field (i.e., sequence numbers range from 0 to 31), match each ARQ protocol with its maximum permissible (Sender Window, Receiver Window) to avoid ambiguity in frame recognition.
| Column – A (Protocol) | Column – B (Window Size) |
|---|---|
| a. Stop-and-Wait ARQ | i. (31, 1) |
| b. Go-Back-N-ARQ | ii. (16, 16) |
| c. Selective Repeat ARQ | iii. (1, 1) |
| iv. (18, 18) | |
| v. (32, 1) |
a – iii, b – v, c – iv
a – iii, b – i, c – ii
a – ii, b – i, c – iii
a – iv, b – ii, c – i
[ Option B ]
In Automatic Repeat reQuest (ARQ) protocols, sequence numbers are used to keep track of frames sent and received, ensuring that lost or out-of-order frames can be identified and retransmitted correctly. Each ARQ protocol imposes limits on the sender and receiver window sizes to avoid ambiguity caused by sequence number.
Stop-and-Wait ARQ is the simplest protocol. In this method, the sender transmits only one frame at a time and waits for an acknowledgment before sending the next frame. Consequently, both the sender and receiver windows are limited to 1, resulting in a window pair of (1, 1).
Go-Back-N ARQ allows the sender to transmit multiple frames before receiving acknowledgments. To prevent confusion when sequence numbers wrap around, the sender’s window size must be 2ⁿ – 1, where n is the number of bits in the sequence field. For a 5-bit sequence number, this gives a sender window of 31, while the receiver window remains 1, producing the window pair (31, 1).
Selective Repeat ARQ allows both sender and receiver to maintain windows that support individual acknowledgment and retransmission of frames. To avoid ambiguity, both sender and receiver windows must be limited to 2ⁿ⁻¹. With a 5-bit sequence number, this results in 16 for both sender and receiver windows, giving the pair (16, 16).
| Protocol Used | Sender Window | Receiver Window | Window Pair |
|---|---|---|---|
| Stop-and-Wait ARQ | 1 | 1 | (1, 1) |
| Go-Back-N ARQ | 31 | 1 | (31, 1) |
| Selective Repeat ARQ | 16 | 16 | (16, 16) |
Q: Match RAID levels in Column I with their description in Column II:
| Column – I | Column – II |
|---|---|
| a. RAID 2 | i. Bit-interleaved parity |
| b. RAID 3 | ii. Mirrored |
| c. RAID 5 | iii. Block-interleaved distributed parity |
| d. RAID 1 | iv. Redundant via Hamming Code |
Choose the correct option:
a – iii, b – i, c – ii, d – iv
a – ii, b – iv, c – iii, d – i
a – iv, b – i, c – iii, d – ii
a – iv, b – iii, c – i, d – ii
[ Option C ]
RAID (Redundant Array of Independent Disks) is a storage technology that combines multiple physical disks into one logical unit for better performance, reliability, or both. Each RAID level has a specific method for distributing and storing data and parity across disks.
| RAID LEVEL | DESCRIPTION | KEY FEATURE |
|---|---|---|
| RAID 0 | Disk Striping, splits data across all disks. | No redundancy, highest performance. |
| RAID 1 | Mirrored. | Data is duplicated on two disks for fault tolerance. |
| RAID 2 | Redundant via Hamming Code. | Uses error-correcting (Hamming) code for fault tolerance. |
| RAID 3 | Bit-interleaved parity. | Data is striped at the byte level with a dedicated parity disk. |
| RAID 5 | Block-interleaved distributed parity. | Data and parity information are distributed across all disks. |
Q: Which of the following is a logical operator in C++?
&&
|
~
&
[ Option A ]
In C++, logical operators are used to combine or negate boolean expressions or conditions to evaluate true or false. The logical operators in C++ are:
Q: Study the following statements:
Statements:
I- A cycle is an open walk with no repeated vertex.
II- A circuit is a closed walk with no repeated edge.
Which of the following is correct?
Only Statement I is true.
Only Statement II is true.
Both Statement I and II are true.
Neither Statement I nor II is true.
[ Option B ]
A Walk in a graph is a sequence of vertices and edges where each edge connects the previous vertex to the next one. It can repeat vertices or edges, there is no restriction.
In graph theory, a Cycle is a closed walk, meaning it starts and ends at the same vertex, and no other vertices or edges are repeated except the first and last vertex being the same.
A Circuit is indeed a closed walk (starts and ends at the same vertex) where no edge is repeated. Vertices may repeat, but edges do not.
Q: Determine output of the following C++ code?
#include<iostream>
using namespace std;
int myfunc(int a);
int myfunc(int a, int b);
int main()
{
int (*fp) (int a, int b);
int (*fp1) (int a);
fp=myfunc;
fp1=myfunc;
cout<<fp(5,6);
return 0;
}
int myfunc(int a)
{
return a;
}
int myfunc(int a, int b)
{
return a*b;
}
6
30
11
5
[ Option B ]
In the given C++ code, two overloaded versions of the function myfunc are defined—one taking a single int parameter and another taking two int parameters. Correspondingly, two function pointers are declared:
When assigning an overloaded function to a function pointer, the type of the pointer determines which overload is selected. Since fp is of type int (*)(int, int), it correctly binds to myfunc(int, int), and similarly, fp1 binds to myfunc(int).
Q: What key principle does the LRU page replacement algorithm use to decide which page to evict?
The page with the smallest page number.
The page that will not be used for the longest time in the future.
The page that was loaded into memory most recently.
The page that has not been used for the longest period of time.
[ Option D ]
In Paging Systems, when a page fault occurs and memory is full, the OS must decide which page to replace.
LRU (Least Recently Used) algorithm evicts the page that has been unused for the longest time, under the assumption that pages used recently are more likely to be used again soon. This is based on temporal locality of reference, a key principle in memory access patterns.
So, LRU page replacement algorithm uses the principle of evicting the page that has not been used for the longest period of time.
Q: A relation schema R is in _________ with respect to a set F of functional dependencies if, A is a super key for schema R for all non-trivial functional dependencies of the form A → B in the closure of F.
BCNF
2NF
3NF
4NF
[ Option A ]
BCNF is an advanced version of 3NF used to remove redundancy caused by functional dependencies. A relation R is in BCNF with respect to a set of functional dependencies F if for every non-trivial functional dependency A → B in F+, the determinant A is a superkey of R.
| Normal Form | Description | Key Characteristics |
|---|---|---|
| 1NF (First NF) | Atomicity | Each column contains atomic, indivisible values; no repeating groups. |
| 2NF (Second NF) | Full Functional Dependency | Every non-key attribute is fully dependent on the entire primary key. |
| 3NF (Third NF) | No Transitive Dependency | No non-key attribute depends on another non-key attribute. |
Q: Let hash function H(K) = (K mod 10) is employed to store in-order, the five keys [40, 27, 19, 48, 7] into set of single digit memory addresses (0-9). If linear probing is used to collision resolution, the key K=7 will be stored at which of the following location?
7
0
8
1
[ Option D ]
Given:
Step-by-step Insertion with Linear Probing:
Insert 40:
Insert 27:
Insert 19:
Insert 48:
Insert 7:
Use linear probing (check next available slot)
Try address 8 → Already taken (by 48)
Try address 9 → Already taken (by 19)
Try address 0 → Already taken (by 40)
Try address 1 → Free
So, 7 is stored at address 1
Q: What is the maximum binary signal transmission rate of a noiseless 3-kHz channel?
12000 bps
6000 bps
3000 bps
1500 bps
[ Option B ]
The maximum data rate of a noiseless channel is determined by the Nyquist Theorem. It defines the theoretical upper limit for data transmission rate in an noiseless channel.
Maximum bit rate = 2×B×log2(M)
Where:
B = Bandwidth of the channel.
M = Number of discrete signal levels (symbols) used.
Given Values:
B=3000 Hz, M=2 (says binary signal and binary means two levels, 0 and 1)
Maximum bit rate = 2 × 3000 × log2(2) and log2(2)=1
So, Maximum bit rate = 2 × 3000 × 1 = 6000 bps.
Q: In the context of standard fuzzy operations on fuzzy sets, which of the following gives (A ∩ B) (x)?
1 - A(x)
min[A(x), B(x)]
max[A(x), B(x)]
1 - B(x)
[ Option B ]
Thank you so much for taking the time to read my Computer Science MCQs section carefully. Your support and interest mean a lot, and I truly appreciate you being part of this journey. Stay connected for more insights and updates! If you'd like to explore more tutorials and insights, check out my YouTube channel.
Don’t forget to subscribe and stay connected for future updates.