The Informatics Assistant (IA) / Suchana Sahayak Paper Solution 2023 by Suraku Academy provides detailed and verified answers for all questions of the Informatics Assistant / Suchana Sahayak exam. While preparing the solution, Suraku Academy put hard work into delivering clear and thorough explanations for students. This resource helps candidates understand concepts deeply and prepares them confidently for the exam. Check out the verified solutions first, then begin your focused learning journey.
| S.N. | Name of Subjects | No. of Questions Asked |
|---|---|---|
| 01. | Computer Fundamentals (Overview, I/O Devices) | 12 |
| 02. | Representation of Data (Number System, Analog Vs Digital, File Concepts) | 08 |
| 03. | Operating System (OS) | 04 |
| 04. | Computer Organization / Architecture | 03 |
| 05. | Networking and Internet Technology (Protocols, Search Engine, WWW, Website, HTML, Video Conferencing, E-Commerce) | 23 |
| 06. | Computer System Security (Viruses, Firewall, Backup, Restoring) | 06 |
| 07. | MS-Office (Word, PowerPoint, Excel), DBMS Software (MS-Access) | 10 |
| 08. | Programming Fundamentals (Algorithms, C Language, OOPs Concepts, IDE) | 24 |
| 09. | Problem Solving, DI, Logical Reasoning, Current Affairs | 60 |
Q: fact (N)
if (N equal 0)
return 1
else
return N * fact (N-1)
The above algorithm is a specific example of ______________.
Selection
Sorting
Recursion
Displacement
[ Option C ]
The given algorithm calculates the factorial of a number N using a function that calls itself with N−1, a clear example of Recursion.
Q: In http://www.ncert.nic.in/textbook/textbook.htm address which is the domain name and which web page is requested?
1. ncert.nic.in
2. http
3. textbook
4. textbook.htm
5. www
Choose the correct answer from the options given below:
1, 5
2, 3
4, 5
1, 4
[ Option D ]
When we access a website, we use a web address (URL) that contains several parts, each serving a specific function, from identifying the protocol used to specifying the exact web page we want to view.
| TERM | DESCRIPTION |
|---|---|
| Protocol | Rules for data transfer. Defines how data is communicated between browser and server. |
| WWW (World Wide Web) | Indicates the section or service of the website. |
| Domain Name | The main address of a website representing the organization or owner. |
| Top-Level Domain (TLD) | Highest-level domain extension. Specifies the domain type (.com, .org, .in, etc.) |
| Path / Directory | Folder location on server. Specifies where the requested page is stored on the website. |
| Web Page / File Name | The actual web file accessed. The specific file the browser displays. |
| URL (Uniform Resource Locator) | The complete address used to locate a web resource. |
In the web address (URL), http://www.ncert.nic.in/textbook/textbook.htm
| PART | MEANING |
|---|---|
| http | Protocol used (Hypertext Transfer Protocol). |
| www | Subdomain (World Wide Web). |
| ncert.nic.in | Domain Name. |
| /textbook/ | Directory or folder within the website. |
| textbook.htm | Web Page Requested. |
Q: Dot matrix printers are also known as serial printers. They print one _______ at a time.
Word
Page
Character
Line
[ Option C ]
Dot Matrix Printers are Impact Printers that use tiny pins to strike an ink ribbon, forming characters or images as a pattern of dots on paper.
They are called Serial Printers because they print one character at a time, moving horizontally across the page.
In contrast, line printers print one entire line at a time, and page printers (laser printers) print a full page at once.
Q: I am a memory device. I am composed of transistors and capacitors. I am able to access the data fast. Who am I?
Dynamic ROM
Static RAM
Dynamic RAM
Static ROM
[ Option B ]
Q: Which is the best software to create a dynamic web page?
HTML
Filmora
Ruby
[ DELETE ]
The question uses the term “software,” but the given options:
Q: Identify the menu tab of MS-Word used to add a table in a document.
Add
Insert
File
Page
[ Option B ]
In MS Word, the Insert Tab is used to add various elements into a document, such as tables, pictures, charts, shapes, headers, footers, and page numbers.
Q: In the diagram given below:
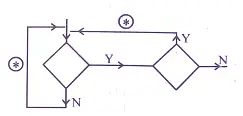
⊛ Indicates ____________ process.
Output
Input
Repetition
Process
[ Option C ]
Q: Development tools like text editors, code libraries, compilers, and testing platforms are available in a _________________ framework of IDE.
Multiple
Different
Single
None of these
[ Option C ]
An IDE (Integrated Development Environment) provides all the necessary development tools such as text editors, compilers, debuggers, code libraries, and testing platforms within a Single integrated framework.
Q: ___________ is mechanism by which one class acquires the properties – data fields and methods of another class.
Class
Encapsulation
Inheritance
Polymorphism
[ Option C ]
Inheritance is a fundamental concept in object-oriented programming (OOP) where one class acquires the properties (data fields) and methods of another class. The class inheriting the properties is called the derived class or subclass or child class, while the class from which it inherits is called the base class or superclass or parent class. Inheritance promotes code reusability.
| OOP’S FEATURE | MEANING |
| Encapsulation | Wrapping data and functions into a single unit (class). Protects data from outside interference. It ensures data security and prevents unauthorized access. |
| Abstraction | Hiding unnecessary implementation details and showing only essential features. It provides simplicity by focusing on what an object does, not how it does it. |
| Inheritance | One class acquires the properties and behaviors of another. It promotes code reusability and establishes relationships. |
| Polymorphism | Ability of the same entity (method/operator) to behave differently based on context. It provides flexibility and reduces code complexity. |
Q: IDE suite consolidates basic tools require to write and ______________ software.
Play
Test
Design
Delete
[ Option B ]
An Integrated Development Environment (IDE) suite consolidates the basic tools required to write, test, and debug software. IDEs provide a comprehensive environment combining code editors, compilers or interpreters, debuggers, and testing tools, all accessible from one interface.
Q: Pen drive is one of the most popularly used device and can be used in _______ port.
SSD
USB
UBS
SD
[ Option B ]
A pen drive, also called a USB (Universal Serial Bus) flash drive, is designed to be inserted into a USB port on computers, laptops, and many other devices.
The USB port allows easy plug-and-play functionality for transferring or storing data, making it the most common interface for pen drives.
| PORT NAME | USED FOR | COMMON DEVICES |
|---|---|---|
| USB (Universal Serial Bus) Port | Data transfer and power supply between computer and external devices. | Pen drives, keyboards, mice, printers, external hard drives, mobile phones. |
| HDMI (High Definition Multimedia Interface) Port | Transmits high-quality audio and video signals. | Monitors, projectors, TVs, gaming consoles. |
| VGA (Video Graphics Array) Port | Transfers analog video signals. | Monitors, older projector. |
| Ethernet Port (LAN Port (RJ-45)) | Connects computer to wired networks. | Network cables, routers, switches. |
| Audio Port (3.5mm Jack) | Sends or receives analog audio signals. | Headphones, microphones, speakers. |
| Thunderbolt Port | High-speed data transfer, video, and power in one cable. | External SSDs, displays, docking stations. |
| SD (Secure Digital) Card Slot | Reads and writes data from SD memory cards. | Cameras, smartphones, SD cards. |
| PS/2 (Personal System/2) Port | Connects input devices (older interface). | Keyboards and mice (legacy systems). |
Q: QR consists of three distinct squares. First two are on the sides of the top and the last one is on the ___________ of the bottom.
Left
Top
Right
Center
[ Option A ]
A QR Code (Quick Response Code) has three position-detection squares that help scanners identify the orientation of the code.
These position markers allow QR readers to quickly detect, align, and decode the information, regardless of the code’s angle or rotation.
Q: Without an IDE, a developer has to select, deploy, integrate and manage all of them ___________.
Virtually
Graphically
Separately
None of these
[ Option C ]
An IDE (Integrated Development Environment) provides a single platform where developers can write, compile, debug, and manage code. Without an IDE, a developer must handle each tool Separately:
Q: _________ is the separation of the logical view of data from its implementation.
Control Structure
Data Abstraction
Testing
Initialization
[ Option B ]
Data Abstraction is the separation of the logical view of data from its implementation details. It allows users to interact with data at a high level without needing to understand the complex underlying details of how data is stored or manipulated. For example, in a database, users can query employee names and salaries without knowing the underlying storage structure or file formats.
Q: During May 2017, a very popular malware infected almost 2 lakh computers around the world. It demanded payments in Bitcoin crypto currency. It made its victims cry. It is known as _____________.
Wanna Cry
Baby Cry
Crypto
Node Cry
[ Option A ]
WannaCry was a ransomware attack that occurred in May 2017, infecting over 2,00,000 computers across 150 countries. It encrypted users’ data and demanded payment in Bitcoin cryptocurrency to restore access, hence the name “WannaCry” because victims were left helpless.
Q: Which geometrical figure represents for Input/Output operation of an algorithm?
Diagonal
Circle
Rectangle
Parallelogram
[ Option D ]
In flowchart representations of algorithms, the Parallelogram is used to represent Input-Output operations.
| SYMBOL | USED FOR | DESCRIPTION |
|---|---|---|
| Oval | Start / End | Represents the beginning or termination of a process. |
| Rectangle | Process | Represents a process, task, or operation to be performed. |
| Parallelogram | Input / Output | Represents input or output operations, such as reading data or displaying results. |
| Diamond | Decision | Represents a conditional or decision-making step. |
| Connector | Small Circle | Connects different parts of the flowchart. |
| Arrow | Flowline | Shows the direction of flow from one step to another. |
| Rectangle with wavy base | Document | Represents a document or report. |
| Rectangle with double-struck sides | Predefined Process | Represents a subroutine or predefined process. |
Q: Repeated division method by 2 is used to convert _________ to _________.
Decimal, Binary
Binary, Decimal
Decimal, Decimal
Binary, Binary
[ Option A ]
The repeated division method by 2 is used to convert a decimal (base 10) number into a binary (base 2) number.
Steps:
1. Divide the decimal number by 2.
2. Record the remainder.
3. Use the quotient for the next division by 2.
4. Repeat until the quotient becomes 0.
5. The binary number is formed by reading the remainders from bottom to top.
Q: Operating system allows the file system to –
Rearrange the characters of the files.
Create, Access, Maintain a directory and protection of file from unauthorized access.
Change the extension of the file.
Transferring files from one computer to another.
[ Option B ]
The File System in an Operating System (OS) provides a way to store, organize, and manage files on storage devices. It allows the system to:
Q: In MS-DOS, when power is turned on, BIOS does the following tasks.
Choose the answer with correct sequence of tasks from the option given below:
5, 4, 2, 3, 1
2, 5, 3, 4, 1
5, 2, 4, 1, 3
2, 3, 5, 1, 4
[ Option C ]
When a computer is powered on, the BIOS (Basic Input/Output System) is responsible for initializing hardware, performing system checks, and loading the operating system into main memory so that the computer can start functioning.
| STEP | TASK | DESCRIPTION |
|---|---|---|
| 1 | Self-Test (POST) | BIOS performs Power-On Self-Test to check hardware components and system integrity. |
| 2 | Load Boot Loader | BIOS loads a small portion of OS called the boot loader from the storage device. |
| 3 | Load Boot Loader into Main Memory | The boot loader is loaded into RAM so it can start execution. |
| 4 | Pull Rest of OS | Boot loader fetches the remaining operating system from disk into memory. |
| 5 | Store OS in Main Memory | The rest of the OS is stored in RAM, completing the loading process so the system can run. |
Q: Which amongst the following is not a search engine?
www
duckduckgo.com
bing.com
yahoo.com
[ Option A ]
WWW (World Wide Web) is not a search engine, it is a system of interlinked hypertext documents (collection of websites) accessible via the Internet. It is the platform on which websites and search engines operate.
A Search Engine is a software system that helps users find information on the Internet. It works by crawling web pages, indexing their content, and then retrieving the most relevant results when a user enters a query.
Search engines use algorithms to rank web pages based on factors like keywords, content quality, backlinks, and user engagement. The list of some important search engine are:
| SEARCH ENGINE | DESCRIPTION |
|---|---|
| The most widely used search engine, known for its fast, accurate, and AI-powered search results. | |
| Bing | The default search engine for Windows and Microsoft Edge, providing web, image, and video search. |
| Yahoo! | One of the earliest search engines, now uses Bing’s technology for search results. |
| DuckDuckGo | Focuses on user privacy and does not track user data or search history. |
| Baidu | The leading Chinese search engine, offering web, image, and multimedia search services. |
| Yandex | A popular Russian search engine offering services like maps, translation, and email alongside web search. |
| Ask.com | A question-answer–based search engine that also provides web search results. |
| Ecosia | An eco-friendly search engine that uses its ad revenue to plant trees. |
Q: Which amongst the following is not a way to protect the system from malware?
Opening the pop-ups
Firewall Protection
Avoid using the Public Wi-Fi
Taking a Regular Backup
[ Option A ]
OPENING POP-UPS is not a way to protect your system, in fact, it is one of the most common ways malware spreads. Pop-ups may contain malicious links, fake ads, or phishing content that can install harmful software on your device.
To stay protected from malware, never click on suspicious pop-ups, use firewalls and antivirus software, and regularly back up important data.
Q: The __________ keyboard of an operating system uses a fixed QWERTY key layout. This can be exploited by keylogger but are still safe than normal keyboard hardware.
On Screen
Online Virtual
Software
Semi-Soft
[ Option A ]
The On-Screen Keyboard is a Virtual Keyboard provided by an operating system that displays QWERTY keys on the screen that allows users to input text by clicking keys using a mouse or touch input instead of a physical keyboard.
Although keyloggers can exploit it by recording screen activities, it is still safer than hardware keyboards, which can be compromised by physical keyloggers.
Q: _________ is a complete software of a third party that is installed on the host computer and can be used by the browser for multiple functionalities.
Firewall
Add on
Plug-in
Extension
[ Option C ]
A Plug-In is a complete software component developed by a third party that is installed on a host application, such as a web browser, to extend its capabilities.
Plug-Ins allow browsers to perform additional functions like playing videos, displaying PDFs, or running multimedia content. Examples include Adobe Flash Player, Java Plug-in, PDF Viewer etc.
Plug-Ins differ from Add-Ons or Extensions, which are usually smaller tools that modify or enhance the browser’s behavior, while plug-ins provide additional functionality through external software integration.
Q: Virtual memory is a memory management technique where –
Main memory can be used as secondary memory.
Only secondary memory is used.
Secondary memory can be used as main memory.
Data transfer is restricted between main memory and secondary memory.
[ Option C ]
Virtual Memory is a technique where part of secondary storage (HDD/SSD) is used by the computer as if it were an extension of the main memory (RAM).
The Operating System (OS) manages this process using paging or segmentation, ensuring smooth performance even when physical memory is limited.
Q: Binary file contains machine readable characters in ____ and ____ format.
1,0
Alphabets and Numbers
Special Characters and Numbers
Alphabets and Special Characters
[ Option A ]
A Binary File stores data in machine-readable format using binary digits (bits), which are 0s and 1s. These digits represent the on and off states in digital circuits, making it a format that computers can directly read and process.
Unlike Text Files which store alphabets, numbers, and special characters in readable format, binary files store data in a very compact and efficient way using only 0s and 1s.
Q: Consider the Excel formula for the Excel Sheet –
| A | B | C | D | E | |
|---|---|---|---|---|---|
| 1 | 60 | A1 | 75 | A1 | =if(A1=C1,”T”,”F”) |
| 2 | 70 | A2 | 70 | A2 | =if(A2=C2,”T”,”F”) |
| 3 | 90 | A3 | 90 | A3 | =if(B3=D3,”T”,”F”) |
What will be the output in column no.5?
| F |
| F |
| F |
| T |
| T |
| F |
| F |
| T |
| T |
| T |
| T |
| T |
[ Option C ]
Q: An __________ is a homogenous structure and starts with _________ index number.
Strings, One
Dictionary, Zero
Array, Zero
Array, One
[ Option C ]
An Array is a Homogeneous Data Structure, meaning it stores elements of the same data type. In most programming languages like C, C++, and Java, array indexing starts from 0.
Q: All the different components which make up the processor have to be condensed to fit in the smart phone. It is known as ___________.
Touch on a chip
Memory on a chip
Processor on a chip
System on a chip
[ Option D ]
System on a Chip (SoC) is a highly integrated microchip that contains all the essential components of a computer or smartphone including processor cores (CPU), memory (RAM and ROM), Graphics Processing Unit (GPU), input/output controllers, modems, and other peripherals on a single chip.
SoCs are designed to fit into compact devices like smartphones, enabling them to run efficiently with reduced space, power consumption, and heat dissipation.
Unlike a processor on a chip, which only contains the CPU, an SoC includes multiple functional units to handle computing, graphics, and communication.
Q: Every NIC Card attached to the node of a network has a unique MAC address. This MAC address is of _______ bit address.
48
96
128
256
[ Option A ]
Ethernet networks use MAC (Media Access Control) addresses as their physical addresses, which are permanently imprinted on the Network Interface Card (NIC) by the manufacturer. A MAC address is 48 bits long, equivalent to 6 bytes, and is usually represented in hexadecimal notation.
This unique identifier ensures that devices within the same local network can correctly recognize and communicate with each other.
Q: In a word document, Simrat has to display the list of online sites which can further be used by a student for preparing a research paper on, “The Effect of Social Media on the behaviour of Students.” Which feature of word is the best suitable to prepare the list?
Linking
Bullets
Numbering
Graph
[ Option A ]
To display a list of online sites that students can use as resources, the best feature in a Word document is Linking (hyperlinks). This feature allows embedding clickable links to websites directly in the document, enabling easy access to online resources.
Q: __________ is a network security system designed to protect a trusted private network from an untrusted outside network to which it is connected.
Bridge
Cookies
Firewall
SSL
[ Option C ]
A Firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Its primary purpose is to protect a trusted internal (LAN) network from untrusted external networks like the Internet.
Firewalls can be hardware, software, or a combination of both, and act as a barrier or gatekeeper between networks by allowing or blocking data packets depending on security policies.
Q: How many layers are there in OSI Model?
3
7
4
6
[ Option B ]
The OSI (Open Systems Interconnection) model is a conceptual framework used to understand and standardize how different networking systems communicate over a network. It divides network communication into 7 layers, each serving a specific function.
| OSI LAYER | DATA UNIT | DESCRIPTION | DELIVERY |
|---|---|---|---|
| Physical | Bits | Transmits raw binary data over physical medium and defines cables, connectors, voltages, and signals. | Node to Node |
| Data Link | Frame | Provides error detection and correction and reliable transfer between adjacent nodes and handles MAC addressing. | Node (Hop) to Node (Hop) |
| Network | Packet | Determines the best path for data transmission and handles logical addressing (IP Addresses) and routing. | Host to Host |
| Transport | Segment | Ensures reliable data transfer, flow control and error recovery, TCP and UDP operate here. | Process to Process / End-to-End |
| Session | Data | Manages sessions and connections between applications, establishes, maintains, and terminates sessions | Process to Process / End-to-End |
| Presentation | Data | Translates, encrypts, compresses, or formats data for the application and ensures data is in usable form. | Process to Process / End-to-End |
| Application | Data | Provides network services to end-user applications like email, file transfer, and web browsing. | End-to-End |
Q: Out of the following topologies which is the least secured and reliable?
Mesh
Star
Tree
Bus
[ Option D ]
In a Bus Topology, all computers are connected to a single central cable called the bus or backbone. Data sent by one computer is received by all others on the same network segment. This design makes it simple and inexpensive, but also less secure and less reliable compared to other topologies.
Network Topology refers to the physical or logical arrangement of computers, cables, and other devices in a network. It defines how nodes (computers, printers, switches, etc.) are connected and how data flows between them. There are two main types:
Choosing the right topology affects network performance, scalability, cost, and reliability.
| TOPOLOGY TYPE | DESCRIPTION | KEY POINTS |
|---|---|---|
| Bus Topology | All computers are connected to a single central cable called the bus or backbone. |
|
| Star Topology | All nodes are connected to a central hub or switch. Communication passes through the hub. |
|
| Ring Topology | Each computer is connected to two others, forming a closed loop. Data travels in one direction (or both in dual ring). |
|
| Mesh Topology | Every computer is connected to every other computer. |
|
| Tree (Hierarchical) Topology | Combination of star topologies arranged in a hierarchical structure. |
|
| Hybrid Topology | Combination of two or more different topologies (e.g., star-bus or star-ring). |
|
Q: IDE is basically an environment of tools like _____________.
Text Editor
Debugger
Compiler
All of these
[ Option D ]
IDEs is a software application that provides comprehensive facilities to computer programmers for software development, combining essential tools like code editors, compilers, debuggers, and build automation into a single interface.
Q: LCD Panels or flat panel display uses the property of ____________.
Fiter
Thickness
Light
Size
[ Option C ]
LCD (Liquid Crystal Display) panels work on the principle of light modulation. The main job of an LCD is to "modulate" light, not generate it.
Instead of producing light by themselves, LCDs use a backlight behind the panel. The liquid crystals in the display control how much light passes through to create the images you see. To do this, the crystals change their orientation when electricity is applied, allowing more or less light to pass through each part of the display.
| Feature | LCD (Liquid Crystal Display) | LED (Light Emitting Diode) | OLED (Organic LED) | Plasma Display |
|---|---|---|---|---|
| Working Principle | Uses liquid crystals and a backlight to control light passing through color filters. | Same as LCD but uses LEDs as backlight instead of CCFL (Cold Cathode Fluorescent Lamp). | Each pixel emits its own light using organic compounds. No backlight needed. | Uses ionized gas (plasma) cells that emit light when electrically charged. |
| Light Source | Backlight. | LED backlight. | Self-emissive. | Self-emissive. |
| Picture Quality | Good color and brightness, but limited contrast and viewing angles. | Better contrast and color than LCD. Thinner design. | Excellent color accuracy, contrast, and flexible displays. | Very high contrast and color accuracy. |
| Viewing Angle | Moderate, color shifts at wider angles. | Slightly better than traditional LCD. | Excellent viewing angles with no distortion. | Excellent viewing angles. |
| Response Time | Moderate, may cause motion blur in fast scenes. | Faster than LCD. | Very fast, ideal for gaming and motion display. | Fast, suitable for video display. |
| Common Uses | Monitors, budget TVs, laptops. | TVs, monitors, smartphones. | Premium TVs, smartphones, smartwatches. | Older large TVs, professional displays. |
Q: A child has to cross road and reach the school opposite to his house. The child looks on right and left before crossing the road. On observing that no vehicle is coming, he crosses the road and reaches school. What action of algorithm is represented by the child in the above situation?
Input
Output
Selection
Repetition
[ Option C ]
The child's action of looking right and left before crossing the road represents a decision-making process. In algorithms, Selection refers to a choice or decision based on a condition.
Q: The _________ button of the mouse is used to display a menu list of different commands related to the selected graphic component.
Left
Centre
Right
Diode
[ Option C ]
The Right Button is used to open a context menu (shortcut menu) that displays a list of commands or options relevant to the selected item or area on the screen.
The Left Button is mainly used for selection and clicking, while the Centre Button (Scroll Wheel) is used for scrolling.
| MOUSE BUTTON | USE |
|---|---|
| Left | Select, drag, open, execute. |
| Centre | Scroll, opening browser tabs. |
| Right | Show menu/list of commands. |
Q: Web based IDE’s are used to develop interactive websites. _______________ is an example of web based IDE.
Microsoft Visual Studio Code
Ruby
Python
HTML
[ Option A ]
Web-based IDEs are online development environments that allow developers to write, run, and debug code through a web browser without installing heavy software locally.
Microsoft Visual Studio Code (VS Code) is a popular IDE that supports web development, including HTML, CSS, JavaScript, and backend languages. It also has extensions for collaborative web-based development.
Q: On dividing ______ binary number by 11, the output is 10. Identify the correct option.
111
011
110
101
[ Option C ]
To find the binary number that, when divided by 11 (binary), gives a quotient of 10 (binary), we first convert the binary numbers to decimal for easier calculation. The divisor 11 in binary is equal to 3 in decimal, and the quotient 10 in binary is equal to 2 in decimal.
Using the formula for division, Dividend = Divisor × Quotient + Remainder, and assuming the remainder is zero, we calculate the dividend as 3 × 2 = 6. Converting 6 back into binary gives 110.
Therefore, dividing the binary number 110 by 11 results in a quotient of 10, making 110 the correct binary number for this question.
Q: __________ is a networking device that extracts the destination address from the data packet and searches for the destination to send the packet. It sends the signals to only selected device.
Wires
Server
Switch
Hub
[ Option C ]
A Switch is an intelligent networking device used to connect multiple computers or devices within a Local Area Network (LAN).
The switch operates at the Data Link Layer (Layer 2) of the OSI Model and is capable of reading the MAC (Media Access Control) address from each incoming data packet. The switch then forwards the packet only to the specific device (destination) for which it is intended.
This selective forwarding reduces network traffic and collisions, improving overall network efficiency and security.
| DEVICE | FUNCTION | KEY POINT |
|---|---|---|
| Hub | Broadcasts data to all devices on the network. | Less efficient, causes network congestion. |
| Switch | Sends data only to the target device. | Faster, secure, reduces collisions. |
Q: Representation of data in a graphical manner is an important feature of Excel. Identify it. Also give the name of the component depicted below:
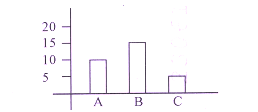
Image, Bar
Graph, Column
Graph, Bar
Graph, Column
[ Option D ]
Q: Solid State Memory Sticks are commonly used in our day to day life. They are available in various storage sizes. Identify the device.
Cache
Compact Drive
Pen Drive
Printer
[ Option C ]
A Pen Drive (USB Flash Drive) is a Solid-State storage device that uses flash memory to store data. It connects to a computer via a USB Port and is commonly used for data transfer, storage, and backup.
Q: The instruction or data fetched from the memory, is stored in the ________ to decode and execute.
MAR
MDR
PC
ROM
[ Option B ]
A Register is a small and very fast storage location inside the CPU (Central Processing Unit) used to temporarily hold data, instructions, or addresses that the CPU needs immediately during processing.
| REGISTER TYPE | DESCRIPTION |
|---|---|
| Program Counter (PC) | Keeps the address of the next instruction the CPU will execute. |
| Instruction Register (IR) | Holds the current instruction that the CPU is decoding and executing. |
| Memory Address Register (MAR) | Stores the address of the memory location that the CPU wants to read or write. |
| Memory Data Register (MDR) | Used to temporarily store data or instructions fetched from memory before the CPU decodes and executes them. It works closely with the Memory Address Register (MAR). |
| Accumulator (ACC) | Temporarily holds data and the results of computations done by the CPU. |
| Stack Pointer (SP) | Points to the top of the stack in memory, used for function calls and local variables. |
Q: Identify the diagram and write the type of conversion the system is performing.
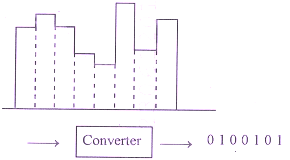
Digital to Analog
Digital to Digital
Analog to Digital
Analog to Analog
[ Option B ]
Q: In a loop of C program, ____________ statement immediately exits a loop, skipping the rest of the body of the loop.
if
else
continue
break
[ Option D ]
In C programming, the break statement is used to immediately exit a loop (for, while, or do-while), skipping the remaining statements in the loop body. When the break statement is encountered, control transfers to the statement immediately following the loop body.
for(int i = 1; i <= 8; i++) {
if(i == 4) {
break; // exits the loop when i equals 4
}
printf("%d ", i);
}
Output: 1 2 3
Q: The binary search algorithm assumes that the items in the array are ___________ and it either finds the item or eliminates half of the array with one comparison.
Unsorted
Sorted
Checked
Selected
[ Option B ]
Binary Search is an efficient search algorithm that works on the principle of divide and conquer:
With each comparison, half of the array is eliminated, making the search faster than Linear Search.
Q: Dev is working on an Excel Sheet. He enters a formula as shown in the figure given below.
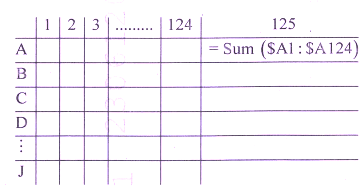
He copies the same formula in rest of 9 (Nine) rows. What will be the output?
Excel will display the same output for each formula in each row.
Excel will display different output for each formula.
Formula is wrong.
Error will be displayed.
[ Option A ]
Q: (111111000101101001)2 = (_______________)16. Choose the correct option –
2 E 1 5 8
2 E 1 5 9
3 F 1 5 8
3 F 1 6 9
[ Option D ]
To convert a binary number to hexadecimal, group the binary digits in sets of 4 (adding leading zeros if necessary), then convert each group to its hexadecimal equivalent and combine.
Step 1:
Group the binary number into 4-bit groups from right to left:
111111000101101001
Since the leftmost group has only 2 bits, we can pad with 2 leading zeros:
0011 1111 0001 0110 1001
Step 2:
Convert each 4-bit group to hexadecimal:
Combine the hexadecimal digits:
(111111000101101001)2 = (3F169)16
Q: Which of the expression correctly defines the statement?
Check whether the values of 3 variables age1, age2, and age3 are equal to each other.
age1 = age2 = age3
age1 == age2 and age2 == age3
age1 != age2 != age3
age1 = age2 and age2 = age3
[ Option B ]
To check if the values of three variables age1, age2, and age3 are equal in C programming (and most languages), you use the equality operator == (Equal to) along with logical AND (&&) to combine multiple conditions.
Remember, the operator = is called assignment operator which is used for assign the value to the left-hand side operand (variable).
Q: In a Data Entry Office, the computer centers are on 1st and 4th floor. Both the centres are connected three LAN. However, the signals take time to travel. Which amongst the following hardware can improve the data transmission?
Modem
Repeater
Router
Computer
[ Option B ]
A Repeater is a networking device used to amplify and regenerate weak signals to extend the transmission distance between network devices. Repeaters operate at the Physical Layer (Layer 1) of the OSI model and do not route or manage traffic. They simply regenerate signals to maintain quality over longer distances.
Modem: A device that converts digital signals from a computer into analog signals for transmission over telephone lines or cable networks, and vice versa. It enables devices to connect to the Internet.
Router: A networking device that directs data packets between different networks, such as between a LAN and the Internet, ensuring that data reaches the correct destination efficiently.
Q: All the search engines use ___________ data where the data is generated from the data itself, such as logical database designs.
Operational
Non-Operational
Meta
None of these
[ Option C ]
All search engines use Metadata, which is data about data. Metadata provides information describing other data, for example, a file’s name, size, date created, author, or content type.
In the context of Search Engines, metadata helps in organizing, indexing, and retrieving web pages efficiently. For instance, HTML meta tags (title, description, keywords) tell search engines what a webpage is about, improving its visibility in search results.
Q: IDE stands for Integrated Development _______________.
Enterprises
Environment
Evolution
Educational
[ Option B ]
IDE stands for Integrated Development Environment. It is a software application that provides comprehensive facilities to computer programmers for software development, combining essential tools like code editors, compilers, debuggers, and build automation into a single interface.
Common examples of IDEs are Visual Studio Code, Eclipse, PyCharm, NetBeans etc.
Q: Can we create an mp4 file of a PowerPoint presentation?
We can create only slides.
We can create only mp3 file.
We can create only animation.
We can create an mp4 file.
[ Option D ]
Microsoft PowerPoint allows you to export a presentation as an MP4 video file. This feature is useful for sharing or uploading presentations as videos without requiring PowerPoint software to view them.
To create an MP4, you go to File > Export > Create a Video, select the quality and settings, and save the presentation as an MP4 file.
Q: Data protection is very essential in today’s digital age where millions of data is created and are illegally used by some. In order to protect data, ___________ grants legal rights to creators for their original work.
IPR
Copyright
Trademark
Licensing
[ Option B ]
Copyright is a form of Intellectual Property Right (IPR) that grants legal protection to creators for their original works such as books, music, software, art, and digital content.
| TERM | DESCRIPTION |
|---|---|
| IPR (Intellectual Property Rights) | A broad term that includes copyright, patents, and trademarks. |
| Copyright | Grants legal rights to creators for original works. |
| Trademark | Protects brand names, logos, and symbols used for commercial identity. |
| Licensing | Legal permission to use someone’s copyrighted work. |
Q: An optical mouse has a light emitting device known as ____________.
Switch
Triode
Diode
Bulb
[ Option C ]
An optical mouse uses a Light-Emitting Diode (LED) as its light source.
Q: Convert the fractional number 0.1011 to decimal. Choose the correct answer.
6875
0.6875
0.6900
6900
[ Option B ]
Each digit after the binary point represents a negative power of 2. By summing these values, we convert the binary fraction to its decimal equivalent. To convert a binary fraction to decimal, use the formula:
0.b1b2b3b4 = b1×2−1 + b2×2−2 + b3×2−3 + b4×2−4
Given:
(0.1011)2 =1×2−1 + 0×2−2 + 1×2−3 + 1×2−4
=0.5+0+0.125+0.0625
=0.6875
So, (0.1011)2 = (0.6875)10
Q: In mesh topology, the requirement of number of wires for ‘n’ number of computers can be calculated using the formula ___________.
(n*(n-1))/2
(n+(n-1))/2
(n*(n+1))/2
(n+(n+1))/2
[ Option A ]
In a Mesh Topology, every computer (node) is connected directly to every other computer in the network. If there are n computers, each computer connects to (n − 1) others.
Number of connections (links / wires) = (n*(n-1))/2. If there are 5 computers, then (5*(5-4)/2) = 5*4/2 =10. So, 10 cables are required to form a full mesh.
Q: Round robin is a method of ___________________ scheduling.
Preemptive Scheduling
Non-Preemptive Scheduling
Both Preemptive and Non-Preemptive
Neither Preemptive nor Non-Preemptive
[ Option A ]
Round Robin (RR) is a preemptive CPU scheduling algorithm used in operating systems.
CPU Scheduling is the method by which an operating system decides which process in the ready queue will get the CPU next. The main goal is to maximize CPU utilization, minimize waiting time, and ensure fair access to processes. The CPU scheduling mainly two types:
Q: __________ signals are discrete and generated by digital modulations.
Analog
Digital
Noise
Bandwidth
[ Option B ]
Digital Signals are discrete signals that represent information using distinct values, often in binary form (0s and 1s). They are generated by digital modulation techniques and are used in computers, digital communication, and networking devices.
Unlike Analog Signals, which are continuous, digital signals are less prone to noise and distortion, making them more reliable for data transmission.
Q: Netbeans have visual components to drag and drop front end components, _______ is an example of it.
Debugger
Plugins
Radio Button
Keypad
[ Option C ]
NetBeans IDE (Integrated Development Environment) provides a visual design interface for building the front end of applications. This allows developers to drag and drop UI components onto a form without writing all the code manually.
Radio Button is an example of a front-end component that can be added using this drag-and-drop feature in NetBeans. Other examples include buttons, text fields, checkboxes, labels, and panels.
Q: Relational operators are accessed by ALU, which gives maximum of __________ possible output.
0
1
2
3
[ Option C ]
Relational operators perform comparisons like equal to, not equal to, less than, greater than, etc. The Arithmetic Logic Unit (ALU) evaluates these comparisons and outputs one of two possible values, typically, 0 (false) or 1 (true).
Thus, the maximum number of outputs the ALU can give for relational operations is 2, representing true or false conditions.
Q: Following steps are followed for a program written in a high-level language by a computer –
1. The program is compiled into object program.
2. Source program is read and loaded in memory.
3. Compiler reads the program loaded in memory.
4. Machine language routines for reading and writing data.
5. Compiler may be removed from memory.
Choose the answer with correct sequence of steps from the options given below:
2, 3, 1, 4, 5
5, 4, 3, 2, 1
3, 2, 1, 4, 5
4, 5, 1, 2, 3
[ Option A ]
When a program written in a high-level language is processed by a computer, it goes through a systematic sequence of operations:
| STEP | PROCESS DESCRIPTION |
|---|---|
| Source program is read and loaded in memory. | The high-level language code is first read and placed into main memory for compilation. |
| Compiler reads the program loaded in memory. | The compiler analyzes or parses the source code for syntax and semantics. |
| The program is compiled into object program. | The compiler translates the code into an object program (machine-readable). |
| Machine language routines for reading and writing data. | The compiler links standard I/O routines (library functions) for program execution. |
| Compiler may be removed from memory. | Once compilation is done, the compiler is no longer needed and is unloaded. |
Q: Class 9th student, Mahi visits the bank for the first time along with her father. She observes that father is issued with a small book which her father tells that it is a cheque book. She opens it and finds some pre-printed information on it. Some of the information printed is same on all the pages but one number is printed in a serial order. She tries to change it. But she is unable to do it. Why she is not able to change it? Identify the specialised feature of the cheque.
OMR Code
BAR Code
QR Code
MICR Code
[ Option D ]
MICR stands for Magnetic Ink Character Recognition. It is a technology used by banks to print a special code at the bottom of cheques. This code uses a unique ink with magnetic particles, which makes it possible for machines to read and verify the printed numbers quickly and securely.
Mahi cannot change or alter this code because magnetic ink and special fonts are used, which prevent tampering or duplication.
Q: When a user initiates multiple process to the computer then the computer follows FIFO method. The expansion of FIFO is
Formula In Formula Out
First In First Out
Figure In Figure Out
Flash In Flash Out
[ Option B ]
FIFO (First In First Out) is a scheduling or data handling method where the first process or item that enters the queue is the first one to be processed or removed. It works much like a queue where the earliest request is served before others.
Q: Soham has created a word document on the topic G20. He has written text matter, images and a table containing, the list of countries and the dignitaries who visited India during G20 Summit. His friend tells him about a term of computer which is generally used by the printers. The term is WYSIWYG. The full form of it is _______________.
What You Set is What You Get
What You See is What You Get
What You Simplify is What You Generate
What You Send is What You Generate
[ Option B ]
WYSIWYG stands for "What You See is What You Get." The term WYSIWYG is used in computing, especially in word processors, desktop publishing, and page layout software.
Q: Identify the gateway for simple internet connectivity at homes.
Internet Service Provider (ISP)
Server
LAN
WAN
[ Option A ]
For simple internet connectivity at home, the gateway that allows users to connect to the Internet is typically provided by the Internet Service Provider (ISP).
When you access the internet from your home (through Wi-Fi, broadband, or mobile data), your ISP provides the necessary network connection, IP address, and routing to link your local network to the global Internet. Some examples of ISP are BSNL,VI, Airtel, Jio, ACT, Hathway, etc.
Q: The preprocessors in C are defined with ________________ character.
/
#
*
$
[ Option B ]
In C programming, Preprocessor Directives are lines included in the code that are processed before compilation. These directives always begin with the # (Hash) symbol. Examples of commonly used preprocessor directives starting with # include, #define, #ifdef, #ifndef etc.
| PREPROCESSOR DIRECTIVE | DESCRIPTION |
|---|---|
| #include | Includes standard or user-defined header files in the program. |
| #define | Defines a macro or symbolic constant. |
| #undef | Undefines a previously defined macro. |
| #ifdef | Checks if a macro is defined, includes code if true. |
| #ifndef | Checks if a macro is not defined, includes code if true. |
| #if | Tests a compile-time condition, includes code if true. |
| #else | Specifies alternative code if #if or #ifdef condition is false. |
| #elif | Combines else and if in conditional compilation. |
| #endif | Ends the conditional directive started by #if, #ifdef, #ifndef. |
| #error | Generates a compilation error with a message. |
| #pragma | Provides special instructions to the compiler. |
| #line | Changes the reported line number and filename for errors. |
Q: ‘Organising the data in a software so that the information is relative to multiple files using a search method.’ Which are the most important features of the software that enable to filter the data. Identify the best option for it.
Access, Query
Word, Find
PowerPoint, Selection
Access, Find
[ Option A ]
Access is a database software used to store, organize, and manage related data efficiently. Query is a powerful feature in Access that allows users to filter, search, and extract specific information based on certain conditions.
Q: ___________ is an example of impact printers.
Laser Printer
Inkjet Printer
Deskjet Printer
Dot Matrix Printer
[ Option D ]
A Printer is an output device that produces a hard copy of text, images, or graphics from a computer or other digital devices.
An Impact Printer is a type of printer that creates images on paper by physically striking an ink ribbon against the paper, similar to how a typewriter works.
Dot Matrix Printers use several tiny pins in a print head. When these pins hit the inked ribbon, they form letters, numbers, or graphics as patterns of dots. This technology is called "Dot Matrix" because the printed results are actually made up of small dots, arranged in a grid (matrix).
| Category | Definition | Type | Description |
|---|---|---|---|
| Impact Printers | Print by physically striking an ink ribbon against the paper. | Dot Matrix Printer | Uses pins to strike ribbon; prints text / graphics; good for multi-part forms. |
| Daisy Wheel Printer | Characters embossed on a wheel; prints letter-quality text. | ||
| Line Printers | Prints one entire line at a time; high-speed printing. | ||
| Non-Impact Printers | Print without physically striking the paper; uses ink, laser, or heat. | Laser Printer | Uses laser beams and toner; prints a full page; high-quality output. |
| Inkjet Printer | Sprays tiny ink droplets; high-resolution; suitable for images. | ||
| Thermal Printer | Uses heat to transfer ink or burn images; used for receipts/labels. | ||
| 3D Printers | Create 3D objects layer by layer from digital models. | 3D Printers | Builds objects layer by layer using plastic, resin, or metal. |
| Multifunction Printers (MFPs) | Combine printing, scanning, copying, and sometimes faxing in one device. | MFPs | All-in-one devices for office / home use; save space and cost. |
Q: In LAN, connectivity can be created using Wi-Fi, or _____________ cables.
TV
Radio
Mobile
Ethernet
[ Option D ]
In a Local Area Network (LAN), devices can be connected either wirelessly using Wi-Fi or wired using Ethernet Cables. Ethernet cables provide a reliable, high-speed, and stable connection between computers, printers, switches, and other network devices within the LAN.
Q: ___________ converts the analogue voice signals into digital and then transmitting them over the broadband line.
Video Conferencing
VOIP
Chatting
Website
[ Option B ]
Voice over Internet Protocol (VoIP) technology converts analog voice signals into digital data and then transmits them over broadband internet lines. This digital conversion allows voice communication to be sent as packets over IP networks rather than traditional telephone lines.
Q: Which amongst the following is qualitative data?
Size of Household
Gender
Eye Color
Age Groups
[ DELETE ]
Q: public class Person
String name
String telephone
String email
//class methods
initialize()
//code for initialize
public print()
public Name Getname()
return Name
public String Getemail()
return email
public String Gettelephone()
return telephone
What will be access specifier of the field of the above class?
public
private
public-private
None of these
[ DELETE ]
Q: Which of the following is not a logical operator?
Check
AND
OR
NOT
[ Option A ]
Logical operators are used in programming and algorithms to perform decision-making based on true or false of conditions.
| LOGICAL OPERATOR | MEANING |
|---|---|
| AND | True if both conditions are true. |
| OR | True if at least one condition is true. |
| NOT | Reverses the logical state, true becomes false, false becomes true. |
Q: All the information on the internet is passed using _____________ switching method.
Portable
Packets
Pouch
Primary
[ Option B ]
All information transmitted over the Internet uses the Packet Switching method. In packet switching, data is broken into small packets before being sent across the network.
Switching Techniques are methods used in network communication to transfer data from a source device to a destination device across a network. They determine how data travels, whether through a dedicated path, divided into packets, or stored temporarily before forwarding.
| SWITCHING TECHNIQUE | DESCRIPTION | KEY POINTS |
|---|---|---|
| Packet Switching | Data is divided into small packets, each sent independently over the network and reassembled at the destination. | Efficient use of bandwidth, reliable, flexible routing, used in Internet. |
| Circuit Switching | A dedicated communication path is established between sender and receiver before data transfer begins. | Guaranteed constant connection, low latency, used in traditional telephone networks. |
| Message Switching | Entire message is stored and forwarded from one intermediate device to another. | No dedicated path needed, can handle large messages, may cause delay due to store-and-forward. |
| Cell Switching | Data is broken into small fixed-size cells and transmitted through the network. | Combines benefits of packet and circuit switching, predictable delay, suitable for real-time applications. |
Q: _________ is an example of analog signal and ___________ is an example of digital signal, respectively.
Smell, Scanning
Scanning, Smell
Smell, Speech
Word Document, Speech
[ Option A ]
Analog Signals represent continuous data and real-world phenomena such as smell, speech, temperature, or pressure that vary smoothly.
Digital Signals are discrete and represent data in binary form, such as scanning, which converts images or documents into digital data.
Q: IPSEC, IP Encapsulation and Tunneling are the technologies used in ____________ only.
Intranet
TCP
VPN
Internet
[ Option C ]
IPSEC, IP encapsulation, and tunneling are technologies used primarily in Virtual Private Network (VPN) to securely transmit data over public or untrusted networks like the Internet.
Q: Which of the following comes under remote login?
1. Video Conferencing
2. Talking on Phone
3. Telnet
4. Any PC
Choose the most appropriate answer from the options given below:
Only 1
1 and 2
Only 3
3 and 4
[ Option C ]
Remote Login allows a user to access and control a computer from a different location over a network, typically the Internet. Telnet (Terminal Network) is a protocol used for remote login, allowing users to log in to a remote computer and execute commands as if they were physically present. Telnet uses Port 23.
Q: Anuj is trying to transfer money to an agency from his bank. On trying multiple times, connection to the bank failed. Because of the financial transactions, certain cookies helps to terminate the session where there is a time-out. These cookies are known as _______ cookies.
E-commerce
Session
Authentication
E-banking
[ Option B ]
A Cookie is a small text file stored on a user’s computer by a web browser when visiting a website.
Cookies store information about the user's interactions and preferences on the site to provide a better personalized experience. They help websites remember login status, items in shopping carts, user settings, and track user activity for analytics or advertising.
Session Cookies are temporary cookies that are created when a user starts an online session and are automatically deleted when the browser is closed or the session expires.
| COOKIE TYPE | DESCRIPTION | EXAMPLE |
|---|---|---|
| Session Cookie | Temporary cookies that store data only for a single session. They are deleted automatically when the browser is closed. | Used in online banking, shopping carts, or secure login sessions. |
| Persistent Cookie | Remains stored on the user’s device even after the browser is closed. They help in remembering user preferences or login details for future visits. | Used for remember me features or language settings. |
| Secure Cookie | Transmitted only over encrypted HTTPS connections. | Safeguard sensitive information like login credentials. |
| HttpOnly Cookie | Not accessible via JavaScript, used to reduce cross-site scripting attacks. | Used to store session identifiers securely. |
| Third-Party Cookie | Created by domains other than the one the user is visiting, usually for advertising or tracking purposes. | Used in online ads and analytics tools. |
Q: Every OS has a __________ which permanently resides in the main memory of the computer to perform some of the basic functions.
Centre
Kernel
Hardware
Node
[ Option B ]
The Kernel is the core part of an operating system that permanently resides in main memory (RAM).
Q: Each file can be accessed through a file mode. These file modes decide what action can be performed in the file. If the file mode is <r> then we can only _________ the contents of the file.
Read
Write
Delete
Overwrite
[ Option A ]
File modes control the type of access you have to a file. When a file is opened in the mode <r>, it means the file is opened for reading only. In this mode, you can only view or read the contents of the file, but you cannot make any changes like writing, deleting, or overwriting the file.
| FILE MODE | OPERATIONS ALLOWED | DESCRIPTION |
|---|---|---|
| r | Read | Open for reading only. File must exist, otherwise, error occurred. |
| w | Write | Open for writing only. Overwrites existing file or creates new file if it does not exist. |
| a | Append (Write) | Open for appending. Data written will be added to the end. Creates file if it does not exist. |
| r+ | Read and Write | Open for both reading and writing. File must exist, otherwise, error occurred. |
| w+ | Read and Write | Open for reading and writing. Overwrites or creates new. |
| a+ | Read and Write | Open for reading and appending. Creates file if it does not exist. |
| rb | Read Binary Data | Open for reading in binary mode. File must exist. |
| wb | Write Binary Data | Open for writing in binary mode. Overwrites or creates new. |
| ab | Append (Write binary data) | Open for appending in binary mode. Creates file if doesn't exist. |
Q: An unauthorized real time interception or monitoring of private communication between two entities over a network is called –
Eavesdropping
Snooping
Phishing
Virus
[ Option A ]
In network security, communication between two devices can be intercepted by malicious users. Eavesdropping is the unauthorized real-time interception or monitoring of private communication between two entities over a network. It can involve listening to voice calls, reading emails or data transmissions without consent, exploiting unsecured or weakly secured communication channels.
Phishing : Fraudulent attempt to obtain or steal sensitive information like passwords.
Virus : Malicious Software (Malware) designed to damage or disrupt systems.
Q: The right most bit of the Binary numbers is _______.
LBB
LSB
MBB
MSB
[ Option B ]
The rightmost bit of a binary number is known as the Least Significant Bit (LSB). It represents the smallest value in binary positional notation, corresponding to 20=1.
The opposite is the Most Significant Bit (MSB), which is the leftmost bit and represents the largest value place in the binary number, corresponding to 2n-1.
Q: User defined functions in C are written using the keyword _______.
define
Define
def
Def
[ DELETE ]
In C Language, user-defined functions are not written using any specific keyword, instead, user-defined functions are simply declared and defined using the typical function syntax.
Return_Type function_name(Parameter_List)
{
// function body.
}
Q: Which of the following is used while working on touch pad?
Finger
Pencil
Stylus
Gloves
[ Option A ]
A touchpad (trackpad) on laptops and other devices is a sensitive flat surface that detects the movement and position of your fingers to control the mouse cursor on the screen.
Q: The octal number system has a base of ________.
10
8
16
4
[ Option B ]
The octal number system is a base-8 number system, which means it uses 8 digits: 0, 1, 2, 3, 4, 5, 6, and 7. Each place value in octal represents a power of 8.
| Number System | Base | Symbols Used | Example |
|---|---|---|---|
| Binary (Internally used by Computers) | 2 | 0 and 1 | 101001 |
| Octal (Rarely used Today) | 8 | 0 to 7 | 1702 |
| Decimal (Standard Number System used by Humans) | 10 | 0 to 9 | 47921 |
| Hexadecimal (Widely used in Computing for Memory Addresses and Color Codes) | 16 | 0 to 9, A to F Where A = 10 and F = 15 | 8F0AE |
Q: ______________ is a standard machine language into which Java source is compiled.
Interpreter
Object Oriented
Byte Code
Assembly
[ Option C ]
In Java programming, the Java source code (.java) is first compiled by the Java Compiler into Byte Code (.class). Byte Code is a standardized machine-independent code that can be executed on any platform using the Java Virtual Machine (JVM).
Q: While transmission of data from a sender to receiver using Modem on Internet, the data is first converted to ________ from ________.
Analog, Analog
Analog, Digital
Digital, Analog
Digital, Digital
[ Option B ]
A Modem (Modulator-Demodulator) is a device that allows computers to communicate over telephone lines or other analog transmission media.
This process is called Modulation (Digital to Analog) and Demodulation (Analog to Digital), which is why the device is called a MODEM (Modulator-Demodulator).
Q: Read the algorithm and identify the type of sorting used in it.
Set A = 0
WHILE (not sorted yet)
find the smallest unsorted item
swap first unsorted item with the smallest
Set A to A + 1
Binary
Insertion
Selection
Bubble
[ Option C ]
Thank you so much for taking the time to read my Computer Science MCQs section carefully. Your support and interest mean a lot, and I truly appreciate you being part of this journey. Stay connected for more insights and updates! If you'd like to explore more tutorials and insights, check out my YouTube channel.
Don’t forget to subscribe and stay connected for future updates.